Keywords
MR-WHT, Singular Value Decomposition, Schur factorization, PSNR, SSIM, NCC, Transparancy, Robustness
This article is included in the Computational Modelling and Numerical Aspects in Engineering collection.
MR-WHT, Singular Value Decomposition, Schur factorization, PSNR, SSIM, NCC, Transparancy, Robustness
The enormous progress in digital technology and the advancement in processor speed, combined with internet access, augmented the ease with which multimedia content including audio, images, and videos were reproduced and duplicated. As a result, owners of associated metadata must contend with the challenge of safeguarding their digital property against copyright violations and other forms of exploitation. As a result, owners of multimedia content must overcome the challenge of preventing copyright infringement and other types of exploitation of their digital content. Digital watermarking provided an effective method of preventing fraudulent and illegal replication of digital media. However, better and more advanced watermarking techniques are required as the use of multimedia documents grows at an exponential rate. Thus, digital watermarking has evolved into a multidisciplinary research field involving communications theory, signal processing, and multimedia coding.
Digital watermarking1 is a technique for concealing information that is embedded in a multimedia object. The object could be any type of multimedia, such as an invisible signal embedded directly in digital media. Spatial and spectral domain methods are the two most commonly used methods for digital watermarking. The first type of algorithm embeds a watermark by modifying image pixels. The second category, for example the Discrete Cosine Transform, embed watermarks in spectrum coefficients (DCT)2–5 and other different transforms.6–18 Techniques in the spectrum domain are considered to be superior compared with those of the spatial domain. In the least perpetually significant coefficients of a transform of an image in the spectral domain, one can insert a watermark. The watermark can be spread across various transform coefficient bands. This will increase the watermarks’ transparency and prevent watermarked image visual degradation. Additionally, the watermark is distributed unevenly, making it extremely challenging for the hacker to remove it.
One issue with current watermarking techniques is that they struggle with the optimization of imperceptibility and robustness because it has been discovered that these two parameters are incompatible. As a result, many techniques to optimize transparency and robustness19–22 are used in the literature. Genetic-algorithms (GA),23–27 Differential-evolution,28–30 Particle-swarm optimization (PSO),31–34 and fuzzy-logic35,36 are currently used in literature for optimizing the transparency and robustness. A GA was used to find optimum thresholds for quantizing wavelet coefficients.32 Oguz FindiK et al.33 used PSO for watermarking color images. Shieh et al.37 identified a fitness function depending on factors related to robustness and imperceptibility. After DCT transformation, the transformed image is segmented into 8 × 8 and four bands are randomly selected for watermark embedding and given to a fitness function. Following GA, the four robust bands with the highest fitness are used for embedding the watermark. Their performance metrics are found to be improved. Another use of GA is demonstrated by aslantas et al.,9 who used GA to investigate the best watermarking strategy based on SVD. To embed the watermark, multiple scaling factors were applied to the singular values of the original image. Additionally, a GA was used in an embedded method based on the quantization index modulation (QIM) technique.38
Much research has been focused on achieving HVS image characteristics and it has been demonstrated that the DHT has a poor threshold difference for noise processing at low compression quality.39 These facts may aid DHT-based schemes in achieving simultaneous optimum performance, as well as achieving optimal robustness against low quality compression while also having a higher embedding capacity, resulting in better performance than DCT or wavelet-based schemes. As a result, we believe that using Walsh-Hadamard characteristics to design optimal data hiding schemes with a high degree of robustness and imperceptibility is a worthwhile endeavor.
Using a hybridized multiresolution fast Walsh-Hadamard transform and Schur transform with differential evolution, a reliable hybrid watermarking is developed in this paper.
Of all the orthogonal transforms that are currently in use, it has the lowest computational complexity. Functionally identical kernels serve as the foundation for the Walsh-Hadamard transform. The kernel of forward Walsh-Hadamard transform is found by:
The inverse kernel of WHT is given by:
The Walsh-Hadamard transform40 is a square array with orthogonal rows and columns of ones with plus and minus signs. The transform is computed quickly using the successive doubling method and has the advantage of having almost identical forward and inverse kernels and less computational complexity. The algorithm exhibits resilience to compression at low quality levels. Compared to other popular transforms, Walsh-Hadamard is more resilient to image manipulation because the multivalued kernels make it such that the values of the pixels in the block alter by various amounts.41 Therefore, real-time hardware implementation is better suited for it.
If a square matrix A has all linearly independent eigenvectors, then an invertible matrix P exists with the property that P−1AP = Λ, where Λ is a diagonal matrix. However, not all square matrices can be diagonalized. QR factorization or Schur factorization can help to address this weakness. Schur asserts that any invertible matrix can be expressed as the multiplication of the upper triangle matrix (T) with the unitary matrix (U).
For some unitary matrix U and upper triangular matrix T. In matrix T, the diagonal entries of T are the eigenvalues of A.
SVD is a mathematical tool that is frequently used in image watermarking, compression, and retrieval. Every real matrix A, according to this theory, can be broken down into a multiplication of 3 matrices, W, D, F where WWT = I, FFT = I and the largest singular values are contained in the diagonal matrix, S. Zero is the singular value of the matrix above rank r.
In SVD, singular values stand in for the layer’s luminance and singular vectors for the image’s geometry. The largest singular values of the SVD have the greatest energy preservation and resistance to small perturbations, making them immune to the majority of signal processing as well as image compression operations.42
A generation is the term used to describe the population in each iteration of the evolution, which typically begins with a population of randomly chosen individuals. Every member of the population has their fitness assessed once every generation; in most optimization algorithms, the fitness is the value of the objective function. The current population is stochastically selected for the fittest individuals, and each individual’s genome is altered (through crossover and possibly through random mutation) to create a new generation. The following algorithm iteration uses the new generation of candidate solutions. The central concept of DE is a method for generating trial parameter vectors. A vector with weighted difference within two members of the population is accumulated to a third member by DE to create new parameter vectors. If the newly produced vector has a relatively low objective function when compared to the population of predefined member, it will be replaced in the next generation by the vector to which it was compared. The aforementioned generation process can, but does not have to, include the comparison vector. Furthermore, to maintain the record of the growth made during the minimization procedure, the parameter vector xbest, G, which is best is calculated for each generation G, is measured. Consider the watermarking system with real valued properties
The watermarking system has constraints in the form of:
System optimization implies varying the D-dimensional parameter vector.
According to scheme DE1 of Ref. 43 for all vectors Xi, G for j = 0,1,2, …, N − 1, a trial vector (v) is produced in accordance to:
Most emerging watermarking methods employ a single transformation function that must be fine-tuned. Moreover, multiple scaling components are recommended in the literature for fine adjusting because singular values reveal different tolerances to different scaling factors. So multiple scaling factors are proposed in the literature.9 The proposed algorithm contains three steps: a watermark concealing algorithm, a watermark extraction algorithm, and a computation of multiple scaling factor.
This subsection describes the proposed watermarking algorithm based on the hybridized multiresolution fast Walsh-Hadamard transform and Schur transform using DE as shown in Figure 1.
1. The cover image A is subjected to a FWHT2 transform.
The significant coefficients of WHT2 lie in the mid and upper bands of frequency of the translated image. Therefore, the watermark is implanted in the mid and high frequency zones of the image.
2. Apply MR-WHT2 to B, given in Equations 10–13. Multiresolution is applied by row followed by column modification. Row-wise modification results from Equations 10–13:
Column-wise modification results:
3. The multiresolution Walsh-Hadamard transform decomposes image into LL, LH, HL and HH bands.
4. Extract the HH band for watermark embedding.
5. Suppose that the cover image size is R × S. The size of HH band after the MR-WHT2 transform is R × S, where P and Q are and . The HH band is segmented into 8 × 8 blocks and the number of R × S is 0 to m-1 and 0 to n-1, where m and n are and .
6. Apply Schur factorization to each 8 × 8 block of HH band. Schur factorization decomposes images into unitary matrix (U) and upper traingular matrix (T).
7. Employ HEBS (high eigenvalue block selection) to obtain the largest eigenvalue of each each 8 × 8 block and its size is the same as the watermark and denotes it array (C). Apply SVD to array B and w, as given in Equation 14.
8. Amended singular values are obtained from wc and ww given in the equation below:
10. Replace the coefficients in Bnew with high eigenvalue blocks in the T matrix of Schur factorization. The modified upper traingular matrix is denoted by Tnew.
11. Apply the inverse Schur transform.
12. Merge all 8 × 8 blocks to form Hnew.
13. Remap all bands LL,LH, HL and HHnew to form Q.
14. Apply the inverse multiresolution to the Q obtained from the column and row transformation. Undo column-wise modification results.
15. Undo row-wise modification.
16. Perform inverse FWHT2D to obtain the watermarked image D.
The proposed watermarking framework is based on non-blind watermarking, which requires an original image for extraction. The host and the watermarked image are subjected to FWHT2D followed by forward multiresolution to obtain LL, LH, HL, and HH bands, as well as LLW, LHW, HLW, and HHW bands, respectively.
1. Apply Schur factorization to HH and HHW bands.
2. Compute the HEBS in upper triangular matrix of Schur factorization to form a matrix array of M and MW, respectively.
3. Apply forward SVD to M and MW to obtain singular values.
4. Obtain singular values of the watermark from wwa and wc by using Equation 22.
5. Obtain the inverse SVD to extract the watermark.
The proposed work utilizes the DE to search for multiple scaling factors (msfs) in order to strengthen the robustness of the proposed scheme. The logo embedded size is 32 × 32. Therefore, the size of msf’s is 32. If the input population size is 100, then 100 strings of 32 variables is stochastically generated, out of which each 32 string represents a possible solution. The fitness function is computed with the structural similarity (S.S.I.M) among A and D and cross correlation is computed between the original and the extracted watermark.
The strings that provided the higher fitness values after all strings in a generation have been examined are chosen for the upcoming generation. Then, using genetic operators crossover and mutation operators from these strings, the population of the upcoming generation is produced. The aforementioned procedures are repeated until a predetermined stopping criterion, such as the maximum generation number, is met.
The proposed algorithm implements on benchmark images airplane, Zelda, Lena, and Baboon, each 512 × 512 in size. The watermark used is a java cup. The algorithm is implemented on Matlab-2013 (RRID:SCR 001622), 4GB RAM, duo core processor. The transparency of the image which is watermarked is judged by peak signal to noise ratio and is given by:
Here, MSE is the mean square within the original and reconstructed image given in Equation 27.
where, X and Y stand for the gray values of the host and watermarked image; Imax is the maximum intensity of the 8 bit image i.e. 255, and M and N are the height and width of the image. The PSNR values of the watermarked image is compared to algorithms developed by Refs. 44–46, with the proposed algorithm as shown in Figure 3. The high PSNR of the proposed algorithm reveals that the proposed watermarking scheme offers high imperceptibility. As shown in Figure 2, the distortion introduced by watermark is negligible and there is no distinction seen between the host and watermarked images of Zelda, Lena and Baboon.

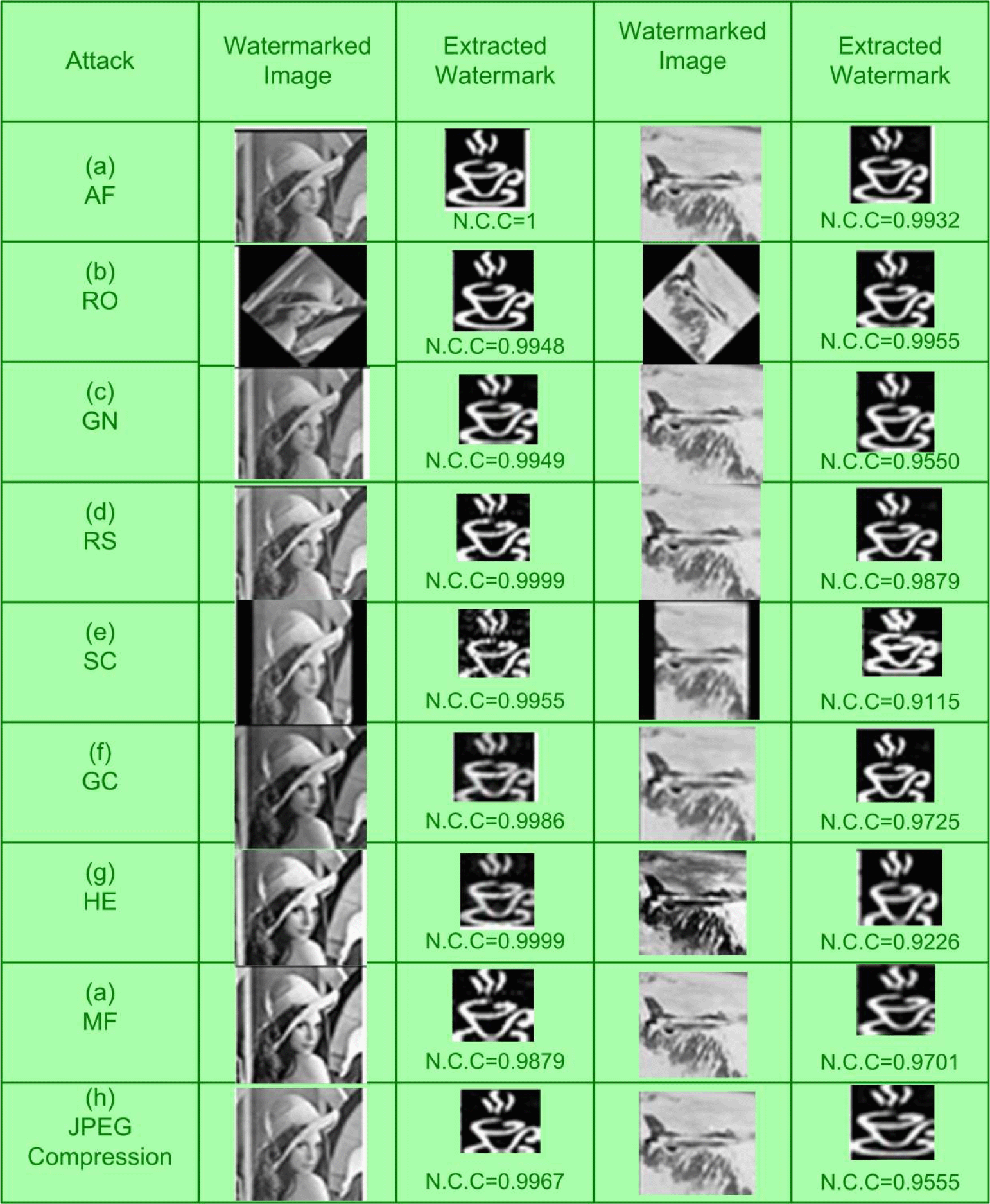
The high peak signal to noise ratio and N.C.C close to 1 signifies that the proposed method is highly imperceptible, as well as robust to attacks.
The settings of the parameter of DE are, F = 0.5, Cr = 0.5, NP = 32, population = 10, maximum number of generations = 200. This section describes the performance of the projected watermarking framework for the various experiments. The Watermarked image is altered when various attacks are considered.
The robustness of proposed framework is contrasted with other methods based on normalized cross correlation. The normalized cross correlation (N.C.C) lies between 0 to 1. If the N.C.C is nearer to 1, the more similar the extorted watermark will be to the embedded one. The proposed algorithm is compared with a pure SVD, simple genetic algorithm, SVD based on a micro genetic algorithm, multiresolution Walsh-Hadamard tranform, and proposed algorithm multiresolution Walsh-Hadamard transform and Schur transform with DE.
The different attacks utilized in the framework of watermarking are:
1. Average filtering: The image which is watermarked is subjected to a low pass mask of 3 × 3 neighborhood. Averaging removes sharp variations in the image such as edges and noise. The extorted watermark is 100% identical to the inserted watermark.
2. Rotation is the important attack during image watermarking. The size of the image typically increases when it is rotated. Therefore, some of the useful information is lost in order to return to its original form. The extracted watermark is 94.48% identical to the inserted watermark.
3. Symmetric cropping: the watermarked image is cropped on both sides. The extracted watermark is 95.55% identical to the original watermark.
4. Histogram equalization: histogram equalization is used to adjust the contrast of the image. The extracted watermark is 99.99% identical to the inserted watermark.
5. Gaussian noise: the marked image is subjected to Gaussian noise, having a zero mean with a normalized variance of 0.01. The extracted watermark is 99.50% identical to the original watermark.
6. JPEG compression: the watermarked image is compressed to a specified ratio of compression of 60%. The extracted watermark is 99.65% identical to the original watermark.
7. A significant attack on image watermarking is scaling. High frequency components are eliminated. Thus, important information could be lost. The image is reduced in size to one-fourth of its original size and placed back in its original location before the extraction process in the proposed watermarking. The proposed watermarking is 99.99% identical to the original watermark. The original watermark and the extracted watermark from the above attacks is shown in Figure 4.
The proposed algorithm is compared with existing optimization algorithms like pure SVD, SVD+GA, SVD+SGA, SVD+μ GA, DCT+DE. The N.C.C values are compared in Table 1.
K. Meenakshi, K. Swaraja: Conception and design of study. Ch. Ushakumari, K. Swaraja: Acquisition, analysis and/or interpretation of data. D. Kishore, K. Meenakshi: Drafting the manuscript and revising.
Figshare:[copyright protection using Multiresolution Walsh Hadamard transform] DOI: 10.6084/m9.figshare.20408937
Data are available under the terms of the Creative Commons Attribution 4.0 International license (CC-BY 4.0).
| Views | Downloads | |
|---|---|---|
| F1000Research | - | - |
|
PubMed Central
Data from PMC are received and updated monthly.
|
- | - |
Is the work clearly and accurately presented and does it cite the current literature?
Partly
Is the study design appropriate and is the work technically sound?
Yes
Are sufficient details of methods and analysis provided to allow replication by others?
Partly
If applicable, is the statistical analysis and its interpretation appropriate?
Yes
Are all the source data underlying the results available to ensure full reproducibility?
Yes
Are the conclusions drawn adequately supported by the results?
No
Competing Interests: No competing interests were disclosed.
Reviewer Expertise: Watermarking
Is the work clearly and accurately presented and does it cite the current literature?
No
Is the study design appropriate and is the work technically sound?
Partly
Are sufficient details of methods and analysis provided to allow replication by others?
Yes
If applicable, is the statistical analysis and its interpretation appropriate?
No
Are all the source data underlying the results available to ensure full reproducibility?
No source data required
Are the conclusions drawn adequately supported by the results?
Yes
Competing Interests: No competing interests were disclosed.
Reviewer Expertise: Image and Video Watermarking, Explainable AI, and Medical Image Analysis
Is the work clearly and accurately presented and does it cite the current literature?
Partly
Is the study design appropriate and is the work technically sound?
No
Are sufficient details of methods and analysis provided to allow replication by others?
No
If applicable, is the statistical analysis and its interpretation appropriate?
Not applicable
Are all the source data underlying the results available to ensure full reproducibility?
No
Are the conclusions drawn adequately supported by the results?
No
Competing Interests: No competing interests were disclosed.
Reviewer Expertise: Image Processing, watermarking
Alongside their report, reviewers assign a status to the article:
| Invited Reviewers | |||
|---|---|---|---|
| 1 | 2 | 3 | |
|
Version 1 16 Nov 22 |
read | read | read |
Provide sufficient details of any financial or non-financial competing interests to enable users to assess whether your comments might lead a reasonable person to question your impartiality. Consider the following examples, but note that this is not an exhaustive list:
Sign up for content alerts and receive a weekly or monthly email with all newly published articles
Already registered? Sign in
The email address should be the one you originally registered with F1000.
You registered with F1000 via Google, so we cannot reset your password.
To sign in, please click here.
If you still need help with your Google account password, please click here.
You registered with F1000 via Facebook, so we cannot reset your password.
To sign in, please click here.
If you still need help with your Facebook account password, please click here.
If your email address is registered with us, we will email you instructions to reset your password.
If you think you should have received this email but it has not arrived, please check your spam filters and/or contact for further assistance.
Comments on this article Comments (0)