Keywords
Graphical Authentication System, PIN, Password, Emoji, Shoulder Surfing
This article is included in the Research Synergy Foundation gateway.
Graphical Authentication System, PIN, Password, Emoji, Shoulder Surfing
In general, graphical passwords are more memorable than text passwords because of the picture superiority effect.1–3 Graphical authentication has been a widely researched topic. At the time of writing this paper, 1,090 articles were retrieved by Google Scholar with the search terms “shoulder-surfing” and “graphical authentication”.
There was an uptrend of publications from 2012 to 2017 which plateaued until 20204 (Figure 1), with mean citations of 15.18 per paper. In dimensions.ai4 the search phrase involving combinations of “emoji”, “picture”, “password” and “authentication” retrieved 587 publications.
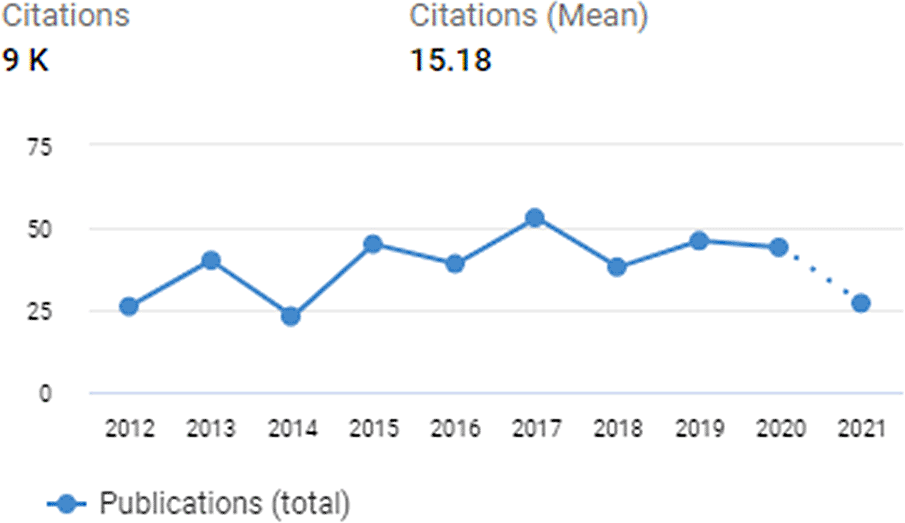
Table 1 shows a comparison of previous works. Emojis have been used in authentication5 but are in general more vulnerable to shoulder surfing attacks (SSAs). DragPIN6 and the methods in7,8 are resistant to SSA. The automatic sliding variant implemented by DragPIN has the advantage of the display not being static, so the displayed state may not necessarily correspond to the password, which makes it shoulder surfing resistant. However, methods7,8 are vulnerable to intersection attacks after multiple recorded observations. DragPIN is resistant to SSAs but uses numbers, which are less memorable than pictures. EmojiAuth5 is not SSA resistant but uses emojis, which are more memorable.
| Reference | Resistance to SSA |
|---|---|
| Srinivasan6 | Yes (auto-sliding variant) |
| Salman Wang, & Li7 | Vulnerable to intersection attack |
| Kasat & Bhadade.8 | Vulnerable to intersection attack |
| Golla, Detering, & Dürmuth5 | No |
Both methods have strengths and disadvantages. Therefore, a modified DragPIN that uses emojis instead of digits addresses both systems’ drawbacks as well as maintaining their respective advantages.
A DragPIN prototype was constructed for testing. A signup screen, as shown in Figure 2, allows a user to create a login and register a 4-digit pin. Users could sign in by choosing either the manual or automatic tabs (Figure 3). Conceptually, the implementation (shown in Figure 3) is similar to the original DragPIN.6
Figure 3 shows the DragPIN interface implementation. A prototype for EmojiAuth was also made: the signup page and login screen with an emoji keyboard are shown in Figures 4 and 5, respectively. Unlike the implementation in the original DragPIN, which had only a choice of 20 emojis, the prototype allowed users to make use of a wider set of emojis.
Operation
In this section, we will describe how the software works. We implemented EmojiSlide (the proposed method) and DragPIN (the reference method) as a web application. All the dependencies required to run the source code are managed by Pipenv version 2020.11.15. The software is provided in the repository as mentioned under the Software availability section. Installation instructions are included in the README.md file archived in release v0.1-beta in the repository. Memory (RAM) 512 MB and 1× CPU cores are the minimum system requirements. Django was the framework used to build this web application. Figure 6 describes the flow of the web application that was used to evaluate the differences between DragPIN and the proposed method (EmojiSlide).
At the start of the program, the user will be prompted to select the authentication method desired, either EmojiSlide or DragPin. Thereafter, users will have two options, which are login or sign up. If the user navigates to the signup page in DragPIN or Emoji-Auth, an empty form is generated and passed to the frontend. The form data received by the backend via POST HTTP request is validated and the user profile is saved in the database, following which users may use their credentials to log in via the earlier chosen method.
The proposed method uses emojis instead of numerics in the reference method, DragPIN. The user registers two 4-emoji passwords. For each 4-emoji password, the system generates six other random emojis, for a total of ten emojis. The set of these ten emojis is the challenge set. The challenge set forms the table (column) indexes used in authentication (shown in Figure 10). The challenge set is fixed per user. This ensures that a user's password cannot be deduced from observing the emojis displayed upon subsequent reloading of the challenge webpage.
To increase memorability and security, cue questions were introduced (Figure 7), which were not present in DragPIN. Users wrote a cue question for each emoji password which also served as the password prompt. Resistance to SSA is increased by having randomly chosen cue questions. Each user must register two cue questions and two passwords, each of which consists of four emojis.
The proposed method was designed as a web application called EmojiSlide.9
The username entry page is shown in Figure 8.
Figure 9 shows that a security measure to prevent Cross Site Request Forgery (CSRF) has been implemented. A CSRF Token is a private, unique, and unpredictable value generated by a server-side application to protect CSRF-vulnerable resources. When the later request is made, the server-side application checks that it has the expected token and rejects it if it is absent or incorrect.
After entering the username, the authentication screen is shown. During authentication (Figure 10), a user chooses either the manual or automatic sliding scheme. The procedure is similar to DragPIN, except that the digits have been replaced with emojis. Figure 10 shows the manual scheme. As an example, the user's emoji password is  ,
,  ,
,  ,
,  . The login process is started by the user mentally choosing an alphabet from the available alphabets. Let the chosen alphabet be ‘D’. One of the D’s in each row is aligned with the password emojis in the correct sequence. The icons look slightly different in Figure 10 due to emojis being customized on different platforms.
. The login process is started by the user mentally choosing an alphabet from the available alphabets. Let the chosen alphabet be ‘D’. One of the D’s in each row is aligned with the password emojis in the correct sequence. The icons look slightly different in Figure 10 due to emojis being customized on different platforms.
Figure 11 shows the automatic sliding variant. The same emoji password example is used. The space bar was used to capture the moment the sliding marker ‘B’ aligned with the password emoji. The “enter” key commenced the sliding of the next row. In this instance, the user pressed the spacebar during alignment and pressed the “enter” key after the marker had slid beyond the password emoji. As a result, the letter ‘B’ was no longer aligned with the password emoji. This misalignment resists SSA.
Ethical considerations
Ethics approval was obtained from the ethics committee of the Multimedia University for the research (approval number EA04420201). The demographics chosen was university students and adults (>18 years old). These would likely be using authentication daily in their lives and have experience with different methods of authentication. An invitation message was sent to potential participants who were acquaintances of the authors. The participants were mostly students in MMU, with a few working adults. The invitation included a website link to a presurvey. Consent was implicit as participants would answer this survey and submit their email if they chose to participate in further testing. No monetary reward was given for participation.
Between 30 to 100 participants is considered a medium-sized sample (Bošnjak & Brumen, 2020). In a review of authentication methods (Binbeshr et al, 2021), most of the user studies (51 out of 55 articles) had between 10 to 50 participants, with 30 being the most common. Thus, in the experiments conducted, the chosen number of participants was 30 or more.
Several questions were chosen in the presurvey to gain insight into the users’ willingness to use emojis as password characters. The survey consisted of six questions (Box 1).
1. On a scale of 0 to 5, 5 being strong and 0 being weak, how strong do you think your password is?
2. How would you rate your ability to recall this password?
3. Would you consider using emojis as your password?
4. Use 6 to 10 emojis only to tell a story about yourself. mine would be: “ ”
”
5. How would you rate your ability to recall this emoji story?
6. Would you still consider emojis as a password?
User testing of EmojiSlide
User testing was done in two phases. Phase 1 tested for login accuracy and time taken, as well as SSA resistance. Phase 2 tested for memorability by measuring login accuracy. Participants in phase 2 were the same as those in phase 1 to achieve reliable memorability statistics.
Phase 1
In phase 1, participants with ages ranging from 18 to 40 were invited to a Google meeting, which was recorded for further evaluation of the scheme’s capability to resist SSA. EmojiSlide’s motivations were briefly described. Then a test user was created. The participant (user) then learned how to login, using each of the variants in both the proposed and reference methods (EmojiSlide Manual, EmojiSlide Auto-sliding, DragPIN Manual, and DragPIN Auto-sliding). After familiarisation, users then registered and attempted to authenticate in each variant. Participants were given three attempts to login. The time taken for a successful authentication attempt was recorded. A usability survey on the proposed method was given after completion. Shoulder surfing was performed on video recordings of user logins. Four "shoulder surfers” went through the familiarisation procedure as described before attempting SSA.
A survey was provided to the participants (the questions can be found in Box 2). Questions 3 to 6 used a Likert scale. The first three questions were for gathering demographic information. The remaining questions were used to ascertain users’ experience with the proposed method.
System usability survey
At the end of the phase 1 experiment, the participants were given a System Usability Survey (SUS) which is a Likert scale (shown in Box 3). Each question’s response was converted to points and the result was graded according to Ref. 10.
1. I think that I would like to use this system frequently.
2. I found the system unnecessarily complex.
3. I thought the system was easy to use.
4. I think that I would need the support of a technical person to be able to use this system.
5. I found the various functions in this system were well integrated.
6. I thought there was too much inconsistency in this system.
7. I would imagine that most people would learn to use this system very quickly.
8. I found the system very cumbersome to use.
9. I felt very confident using the system.
10. I needed to learn a lot of things before I could get going with this system.
Phase 2
In phase 2, held 4-6 weeks later, the same users from phase 1 were invited to re-login to test for password memorability.
Significance testing
Hypothesis testing was performed to compare the differences between EmojiSlide(E) with DragPIN (DP) in both manual (m) and auto (a) variants. The software used was Microsoft Excel version 2011. The factors for comparison are the time taken for login, t and the mean number of intermediate failures, f. The null hypotheses are that there are no differences. The method’s name and variant form the subscript in Table 4, e.g. the time taken for Emojislide manual is tEm. For statistical analysis of results, we applied paired t-tests. A p value of p < 0.05 was considered statistically significant.
The datasets for the user results are available as Underlying data.11–13
A total of 50 participants took part in the presurvey. The questions were not compulsory to answer thus not all questions had 50 responses. In the presurvey, participants were asked to create an emoji story about themselves using six to ten emojis. For question no. 3, ‘Would you consider using emojis as your password?’ (n = 50) about 72% answered Yes or “I am not sure”, and one person (2%) gave a comment about the possibility of emoji passwords being guessed, while 26% answered No (Figure 12). To ascertain their answer with practical experience, those who did not answer “No” went on to create their emoji stories in question 5. After creating emojis, (n = 37) answered the repeated question of ‘Would you still consider using emojis as your password?’ (question 6). Only 1 person answered No, indicating that there was a willingness to try using emoji passwords.
The respondents who created their emoji stories (n = 37) also rated their ability to recall the emoji story they created on a scale of 0 = weak and 5 = strong (Figure 13). Option ‘5’ had the highest number of responses, indicating that most respondents felt confident of their ability to remember their emoji password.
A total of 30 participants took part in user testing. Figure 14 shows the age groups: most participants were aged 20-30 years old (76.7%). Table 2 shows the demographics of the participants.
| Categories | Percentage % |
|---|---|
| Males | 66.66 |
| Females | 33.33 |
| Graduates/Employed | 26.67 |
| Undergraduates | 73.33 |
| Computer savvy users | 26.66 |
| Average computer users | 53.33 |
| Non-frequent computer users | 20 |
Table 3 shows the average time taken to login for successful attempts. Users logged in slightly faster using EmojiSlide (proposed method) compared to DragPIN. Results also showed that login to auto-sliding variants took longer than the manual variants.
| Parameters | Average login time of successful attempts, seconds (s) |
|---|---|
| DragPIN Manual | 19.3 |
| DragPIN Automatic | 30.1 |
| EmojiSlide Manual | 16.7 |
| EmojiSlide Automatic | 29.5 |
Post experiment, users were requested to state whether they would trust the system to resist SSA. Figure 15 shows that 76.7% answered yes, 23.3% were unsure and none answered no, showing that the system was judged capable by most participants.
None of the shoulder surfers were able to get any full PIN or emoji password. They commented that slowing or reversing the recorded videos availed little, especially for the automatic variants. They were only able to obtain two emojis, from three users, which was due to those users pointing their mouse cursor at their desired emoji. All participants logged in successfully within three attempts (100% login accuracy). Most of the mistakes occurred during phase 1, for the DragPIN auto variant where three participants used three login attempts to login.
Figure 16 shows the average successful login rates when the number of intermediate failures before succeeding is taken into account. If a successful login takes one attempt (0 failures), the success rate = 100%, if it takes two attempts (1 failure), the success rate = ½ or 50% and if three attempts (2 failures), success rate = 1/3 or 33.33%. This is calculated per user. The average success rate is shown in Figure 16.
After 4-6 weeks, the login accuracy for both the auto sliding and manual variants ranged between 76.7-78.3% for the reference method and 86.7-91.7% for the proposed method.
Referring to Table 4, the null hypothesis for (1) is that there are no differences in the mean login time between the manual EmojiSlide (E) & DragPIN (DP). The t-test gives t(29) = 2.13, p = 0.04, which shows that the mean login time differs. The mean login time is shorter for the EmojiSlide. However, for (2), the time differences between the autosliding versions of E & DP were not significant.
| Set | H0 | H1 | Number of tails |
|---|---|---|---|
| 1. Login time manual | tEm = tDPm | tEm ≠ tDPm | 2 |
| 2. Login time auto | tEa = tDPa | tEa ≠ tDPa | 2 |
| 3. Number of failures manual | fEm = fDPm | fEm < fDPm | 1 |
| 4. Number of failures auto | fEa = fDPa | fEa < fDPa | 1 |
The null hypotheses for (3) and (4) are that there are no differences in the number of intermediate failures (during Phase 1) in the manual and auto EmojiSlide and DragPIN versions respectively, while the alternative hypotheses are that the EmojiSlide versions have fewer failures. The one tailed t-test for manual variants (3) gave t(29) = 1.99, p = 0.028. The auto versions (4) had t(29) = 2.25, p = 0.016. In Phase 2, hypothesis set (3) gave t(29) = 2.11, p = 0.02 but in hypothesis set (4), the null hypothesis was not rejected. Thus, in Phase 1, EmojiSlide (manual and auto) had a lower number of failures compared to DragPIN, and this trend continued in Phase 2 for the manual variant.
This suggests higher memorability in the proposed method. The login accuracy was higher even though the users had two sets of emoji passwords to remember versus one PIN.
The SUS showed that the average score per user was 88.5% (Excellent). The score distribution is shown in Figure 17.
As the emoji-based implementation was based on one method, whether the memorability gains will extend to other authentication methods is yet undiscovered. Also, the sample comprised mostly young people thus the effect on older adults was not tested. Larger scale testing with a higher number and variety of participants can provide more insight. One of the system’s future upgrades is the use of the most recent version of emojis.
In this paper, a graphical authentication method was proposed where emojis were used in place of numerics and cue questions were added. Results indicate the proposed method and reference method resisted SSA where no passwords were compromised. Passwords remained memorable after 4-6 weeks where the proposed method had a login accuracy of 86.7-91.7% compared to 76.7-78.3% for the reference method. The results indicate that the use of emoji-based stories may have higher memorability than numbers. Personalized cue questions may also aid memorability.
Figshare: Using Emojis in a Shoulder-surfing Resistant Authentication Method, Pre-survey.csv. (Pre-survey results.). https://doi.org/10.6084/m9.figshare.14872062.v1.11
Figshare: Using Emojis in a Shoulder-surfing Resistant Authentication Method, Phase1&2.csv. (User testing results). https://doi.org/10.6084/m9.figshare.17163470.v1.12
Figshare: Using Emojis in a Shoulder-surfing Resistant Authentication Method, SUS.csv (System Usability Survey results.). https://doi.org/10.6084/m9.figshare.14872059.v1.13
Data are available under the terms of the Creative Commons Attribution 4.0 International license (CC-BY 4.0).
Source code for EmojiSlide available from: https://github.com/mahrous-amer/FYP/tree/v0.1-beta
Archived source code at the time of publication: https://doi.org/10.5281/zenodo.55743879
Licence: MIT
This work was supported by the IRFund grant [grant number MMUI/210071], Multimedia University, Malaysia.
An earlier abridged version of this work was presented at the iCatse International Conference on IT Convergence and Security 2021. 14
| Views | Downloads | |
|---|---|---|
| F1000Research | - | - |
|
PubMed Central
Data from PMC are received and updated monthly.
|
- | - |
Is the work clearly and accurately presented and does it cite the current literature?
Partly
Is the study design appropriate and is the work technically sound?
Partly
Are sufficient details of methods and analysis provided to allow replication by others?
Partly
If applicable, is the statistical analysis and its interpretation appropriate?
Partly
Are all the source data underlying the results available to ensure full reproducibility?
No
Are the conclusions drawn adequately supported by the results?
No
Competing Interests: No competing interests were disclosed.
Reviewer Expertise: Information security
Is the work clearly and accurately presented and does it cite the current literature?
Partly
Is the study design appropriate and is the work technically sound?
Partly
Are sufficient details of methods and analysis provided to allow replication by others?
Partly
If applicable, is the statistical analysis and its interpretation appropriate?
Partly
Are all the source data underlying the results available to ensure full reproducibility?
Yes
Are the conclusions drawn adequately supported by the results?
Partly
Competing Interests: No competing interests were disclosed.
Reviewer Expertise: perceptual psychology
Alongside their report, reviewers assign a status to the article:
| Invited Reviewers | ||
|---|---|---|
| 1 | 2 | |
|
Version 1 29 Mar 22 |
read | read |
Provide sufficient details of any financial or non-financial competing interests to enable users to assess whether your comments might lead a reasonable person to question your impartiality. Consider the following examples, but note that this is not an exhaustive list:
Sign up for content alerts and receive a weekly or monthly email with all newly published articles
Already registered? Sign in
The email address should be the one you originally registered with F1000.
You registered with F1000 via Google, so we cannot reset your password.
To sign in, please click here.
If you still need help with your Google account password, please click here.
You registered with F1000 via Facebook, so we cannot reset your password.
To sign in, please click here.
If you still need help with your Facebook account password, please click here.
If your email address is registered with us, we will email you instructions to reset your password.
If you think you should have received this email but it has not arrived, please check your spam filters and/or contact for further assistance.
Comments on this article Comments (0)