Keywords
Internet of Things, cyber-attacks, Internet of Things security, machine learning
This article is included in the Artificial Intelligence and Machine Learning gateway.
This article is included in the Cybersecurity collection.
The rapid growth of the Internet of Things (IoT) has brought transformative benefits across industries, yet it also presents significant security challenges due to the proliferation of connected devices.
This study proposes an artificial intelligence (AI) model leveraging machine learning algorithms to detect and classify multiple types of IoT attacks, including distributed denial of service (DDoS), reconnaissance, brute force, spoofing, and Mirai attacks, using the CICIoT2023 dataset. The dataset was divided into training and testing sets to ensure accurate performance assessment. After training, the models were tested, and their effectiveness was evaluated through metrics like accuracy and confusion matrices.
Among the algorithms used, the decision tree model outperformed than others, achieving an impressive accuracy of 98.34%. In contrast, Bayes classifiers, support vector machines (SVM), and logistic regression achieved accuracy rates of 92%, 91.5%, and 75%, respectively. These results highlight the significant potential of machine learning techniques in detecting and mitigating various IoT attacks, offering promising avenues for enhancing IoT security. The improvement of the performance of the IoT attack detection model using large datasets and the appropriate using deep learning algorithms with their parameters will be our future consideration in the domain.
Internet of Things, cyber-attacks, Internet of Things security, machine learning
The Internet of Things (IoT) is a network of hundreds of millions of gadgets that can communicate with one another with little help from users. IoT attack is a type of cyber-attack that targets systems made up of physical things, cars, buildings, and other objects integrated with software that allows them to exchange or collect data.1 As described by Anwer A. & et al.,2 there were about 28 billion IoT devices in use in 2018. By 2022, this sum is predicted to reach 49.1 billion, and the IoT is projected to reach a display size of approximately ten trillion. IoT is acknowledged as a technique for appropriate mechanisms connected via servers, sensors, and different software.2
According to the Ethiopian Information Network Security Administration (INSA) director report, they saved 23.2 billion birrs by defending against cyber-attacks. During 2022/2023, more than 6,859 cyber-attacks occurred and only 6,768 cyber-attacks got solutions. Banking and financial institutions, national intelligence security services, media institutions, selected governmental institutions, regional offices, health and higher institutions are the most targeted centers. According to the report, website attacks, malware attacks, port scans, distributed denial of service (DDoS), and structured query language (SQL) Injection are the most frequently occurring types of attacks in Ethiopia during 2022/23.3
It is difficult to produce IoT security data that is useful for actual applications for several reasons. Having a vast network made up of multiple actual IoT devices, akin to the topologies of actual IoT applications, is one of the primary issues. Due to the widespread adoption of IoT, its inherent mobility, and standardization limitations, numerous researchers have looked into the risks that IoT devices pose to large corporations and smart towns. As a result, smart mechanisms that can automatically detect suspicious movement on IoT devices connected to local networks are required.2,4 The pervasive growth of the IoT creates an expanding attack surface for malicious actors. Detecting these attacks effectively is crucial for securing IoT systems and protecting sensitive data. This paper explored the use of machine learning (ML) for attack detection in IoT environments, focusing on the challenge of imbalanced datasets and potential solutions.
The IoT has become a crucial component of today’s technological landscape, as it allows various devices and systems to connect and communicate with each other over the Internet. This interconnected network of devices has revolutionized many industries, including healthcare, transportation, manufacturing, and smart homes. The IoT has become increasingly significant in today’s world by connecting everyday objects to the Internet, automating tasks and processes, enhancing data-driven decision-making, and creating new opportunities.
However, the widespread adoption of IoT devices has also introduced new security challenges and vulnerabilities. IoT devices are often designed with limited processing power and memory, making them more susceptible to attacks. Additionally, many IoT devices lack robust security features, such as encryption and secure authentication mechanisms, interconnectedness, and privacy concerns, making them easy targets for cybercriminals. There are different types of attacks targeting IoT devices namely; malware, DoS attacks, man-in-the-middle attacks, botnet attacks, and physical attacks. IoT devices, with their limited processing power, are vulnerable to cyberattacks, making them attractive targets for hackers seeking unauthorized access or control. These devices collect vast amounts of personal data, and inadequate security can lead to serious privacy breaches. Many are integrated into critical infrastructure, meaning attacks can cause widespread disruption and economic damage. Compliance with regulations is essential to avoid legal and reputational consequences. Security flaws in one device can compromise entire networks, emphasizing the need for robust protection. High-profile breaches can erode consumer trust, hinder adoption, and result in significant financial losses. If security risks are not addressed, innovation in IoT may slow down. Ensuring long-term sustainability requires continuous investment in security measures, and collaboration among organizations, developers, and policymakers is crucial for a secure IoT ecosystem.
The main contributions of this work are summarized as:
(1) Prominent result: The proposed model is focusing on evaluating ML algorithms’ performance using unbalanced datasets and the prominent result was resulted. Moreover, the authors also compared the results from the existed related works and performance has been improved.
(2) Automation and efficiency: ML algorithms can analyze large amounts of IoT network data more quickly and accurately than manual methods. This could enable the detection of attacks in real time, enhancing the security of IoT systems.
(3) Scalability: As the number of IoT devices continues to grow rapidly, ML based systems can scale efficiently to handle large networks with numerous devices, ensuring comprehensive attack identification and protection.
Several scholars used various methodologies to carry out studies on cyber-attack detection.
In their study,2 outlined a methodology for identifying suspicious network activity. They achieved a performance result of 85.34% using a random forest (RF) algorithm. Using the NSL KDD dataset, the suggested framework was used, and the results were compared for training, prediction time, specificity, and accuracy.
In their study,5 several detection techniques are assessed using the recently created Bot-IoT dataset. During the implementation stage, seven distinct ML algorithms were employed, with the majority demonstrating exceptional performance. Throughout the deployment, new features were taken from the Bot-IoT dataset.
In their study,6 they used six distinct algorithms RF, Logistic Regression (LR), SVM, NB, K-Nearest Neighbors (KNN), and multilayer perceptron (MLP) to conduct a comparative analysis of IoT cyber-attack detection techniques.
In their study,7 To effectively detect attacks and abnormalities in IoT systems, the authors of the paper compared the performances of numerous ML models. LR, SVM, decision tree (DT), RF, and artificial neural network (ANN) are the ML algorithms that were employed in this case.
In their study,8 they performed IoT behavior classification, monitoring the expected IoT behaviors and evaluating the efficacy of our optimally selected classifiers versus the superset of specialized classifiers by applying them to our IoT traffic traces.
In their study,9 the study attempts to secure IoT devices by employing a Raspberry Pi as a honeypot to mimic IoT devices and verify the user’s intent, examine various attack patterns, and shield IoT devices from known threats. The purpose of these honeypots is to protect various protocols in IoT devices that are susceptible to assaults.
In their study,10 Using an extended topology made up of multiple real IoT devices, they conducted a novel realistic IoT attack dataset, adopting IoT devices as both attackers and victims. They carried out, recorded, and gathered information from 33 attacks against IoT devices, categorized into seven types, and they showed how they could be replicated. Using the CICIoT2023 dataset, they assessed how well ML and deep learning algorithms classified and detected benign or malicious IoT network traffic.
In their study,11 applied a hybrid deep learning technique to handle the problem of uneven data classification in attack detection. Convolutional neural networks (CNNs) and long short-term memory (LSTM) networks are two components of a hybrid deep learning model that the authors suggest using to enhance classification performance. They draw attention to the difficulties that imbalanced datasets present in precisely identifying attacks. CNNs are useful for extracting spatial properties from the data, they say, whereas LSTM networks are better at extracting temporal dependencies from sequential data. The hybrid deep learning model’s performance is compared with that of conventional ML methods by the authors through experimentation on attack datasets that are not balanced. The results demonstrate that the hybrid deep learning approach outperforms traditional methods in detecting attacks in imbalanced datasets, showcasing the effectiveness of combining CNNs and LSTM networks for improved classification accuracy.
In their study,12 explains in detail the many ML methods that are employed to identify IoT botnets. In the IoT ecosystem, botnets pose an increasing threat, as the review emphasizes the significance of IoT security. It covers the many ML techniques and algorithms that have been put forth to identify and lessen IoT botnet threats. To give readers an understanding of the current status of this field of research, the manuscript carefully assesses the advantages and disadvantages of different methodologies. For those working on botnet detection and IoT security, the paper is an invaluable resource overall.
The study,13 examined how ML approaches applied to Industrial Internet of Things (IIoT) systems security are affected by imbalanced datasets. To better understand how class imbalances in datasets impact ML models’ ability to identify security vulnerabilities in IIoT environments, the study looks into how these imbalances may impact model performance and accuracy. Within the framework of IIoT security, it addressed several problems and difficulties associated with unbalanced datasets, including minority class misclassification and biased model predictions. Additionally, to improve the efficacy of machine learning-based security mechanisms in IIoT systems, the book suggests possible approaches and answers to these problems. Overall, the study provided valuable insights into the implications of imbalanced datasets on the security of IIoT and offers recommendations for improving the robustness and reliability of security measures in industrial IoT settings.
However, the security issue of IoT has not addressed yet and further investigations are required. Therefore, we the authors are focusing on such issues to improve the performances of the existing works and evaluating other ML algorithms in this paper.
This study followed crucial steps illustrated in the proposed IoT attack detection architecture to conduct rigorous experiments, as shown in Figure 1 designed by the authors.
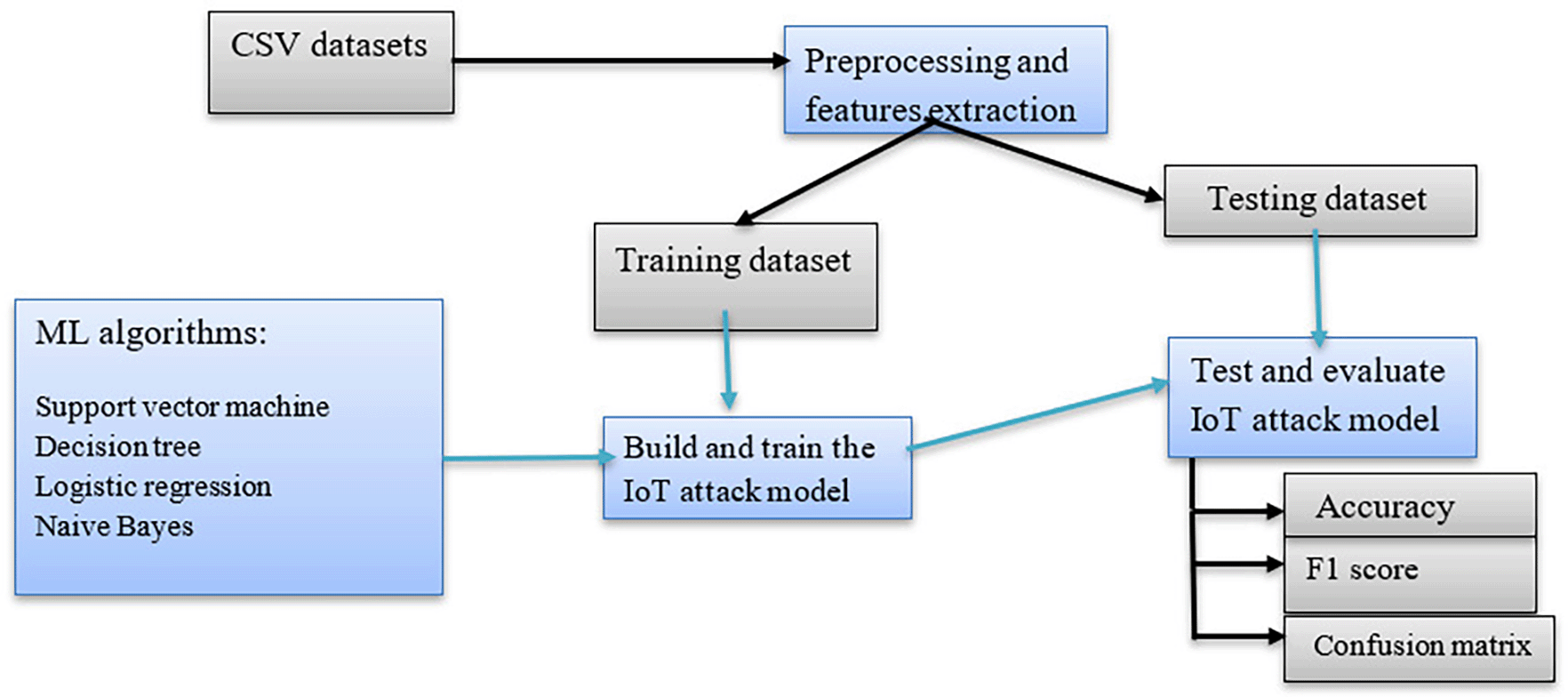
This figure has been created by the author.
One of the most frequent problems faced by ML researchers is locating reliable datasets with the necessary properties. Regardless of the size of the dataset, selecting a specific learning technique is not as crucial as creating a well-cleaned representative dataset.14 In our investigation, we used a distinct IoT attack dataset from the CICIoT2023, which has a total of 221,834 occurrences that were recorded as Comma Separated Values (CSV) files. In our study, 42 relevant features were extracted, and the total dataset was labeled namely Benign Traffic, DDoS, Spoofing, SQL Injection, Recon, and Mirai. The following three key reasons were taken into account why selecting the aforementioned dataset: i) the dataset contains 42 attributes extracted from different categories of IoT attack features; ii) the dataset contains 221,834 dataset instances which are cleaned, imbalanced, and contain the required features as shown in Table 1; iii) the dataset contains raw datasets so that it is possible to generate new features as needed.
Preprocessing data and feature extraction for IoT attack detection with an imbalanced dataset is an important step to ensure the effectiveness of ML approaches. The researcher implemented dimensionality reduction, data splitting, and data cleaning. To ensure its quality and reliability, the researcher handles missing values, outliers, and any inconsistencies in the dataset.
Feature selection involves selecting and transforming relevant features from the raw data to improve the performance of the ML model. The researcher extracted 42 informative features using principal component analysis techniques.
Train-test dataset splits are required before feeding datasets to the learning algorithms. This is because it’s anticipated that learning model(s) would be evaluated using unidentified datasets to assess how well they can forecast new IoT threats. Most studies employed train-test dataset split ratios of 80%:20%.15 However, the study groups could not agree on how much train-test dataset split ratio to use for how many dataset instances. This is why the suggested study chose a dataset split ratio that yields improved training and testing set accuracy for each classifier by using 80%:20% train-test dataset split ratios on each classifier.
As a result, for our model experiment from the total dataset, we have taken 80% (177,467) of the dataset used for training, and 20% (44,367) used for testing our model performance accuracy.
The study conducted extensive experiments using Python to test and train the suggested Supervised ML algorithms using high-speed computing. Python was chosen as the implementation language for the study due to its abundance of libraries and packages tailored for ML research.
We the authors employed four well-known ML algorithms, namely; decision tree, SVM with default parameters, SVM with sigmoid kernel, LR, and Naïve Bayes16–19 to identify IoT attacks.
DTs are versatile and intuitive models that make predictions by recursively splitting the data based on different features. They are known for being interpretable and can handle both categorical and numerical data. We used default DT parameters like Max depth, minimum samples per leaf, splitting criteria, and maximum features per split.
SVM is a powerful algorithm that separates data points into different classes by finding the best hyperplane that maximizes the margin between the classes. The default parameters refer to the default values set by the algorithm, which may vary depending on the implementation. SVM can also utilize different kernels, such as the sigmoid kernel, which allows for non-linear separation of data points. The sigmoid kernel maps the data into a higher-dimensional space to find a decision boundary.
Despite its name, LR is a classification algorithm rather than a regression algorithm. It calculates the probability of an instance belonging to a certain class using a logistic function. It’s commonly used for binary classification problems. To control the degree of regularization, penalizing complex models, and reducing overfitting we used the regularization parameter (lambda). Chooses gradient descent algorithm used to find the optimal model parameters. Sets the maximum number of iterations for the solver to find the optimal parameters.
Naïve Bayes is a probabilistic classifier that calculates the probability of an instance belonging to a particular class based on Bayes’ theorem, assuming that all features are independent. We used the following key parameters to implement the Naïve Bayes algorithm for IoT attack detections. Smoothing parameter (Alpha): Adds a small value to the estimated probabilities to avoid division by zero and improve stability, especially with sparse data. Feature selection: Choosing the subset of features most relevant for classification can improve performance and interpretability.
It’s critical to specify performance metrics appropriate for the task at hand when assessing ML models. We employed the most significant performance metrics for, the accuracy, and confusion matrix to assess our findings.20
Accuracy is calculated as the sum of two accurate predictions (TP + TN) divided by the total number of data sets (P + N). The best accuracy is 1.0, and the worst is 0.00.20
To attain better performance results, we conducted data preprocessing techniques. The dataset is transformed into a structure appropriate for ML using pre-processing data transformation techniques.21 To make the dataset more accurate and efficient, this stage also involves cleaning it by deleting any irrelevant or corrupted data.
We employed various supervised ML techniques, including LR, DT, SVM, and NB, to carry out this investigation. DT outperformed other ML algorithms by achieving accuracy of 98.34%, as shown in Table 2.
Accuracy is one of the most relevant performance evaluation metrics in ML as well as deep learning algorithms. This metric is also deployed in this work, as shown in Table 2 that shows DT was the highest-performing algorithm, followed by NB and SVM with default value. SVM with a sigmoid kernel received the lowest performance score of 69.27%, making it the least effective algorithm. Despite having a high-performance score, NB was notably slower than the other algorithms. Graphically, the performance result is shown in Figure 2.
In addition to accuracy, confusion matrix is also used to evaluate the performance. An N x N matrix, where N is the total number of target classes, is called a confusion matrix and is used to assess how well a classification model performs. The ML model’s predicted outcomes are compared with the actual target values in the matrix. The confusion matrix was obtained when we employed different ML algorithms of SVM, LR, NB, and DT algorithms respectively, as shown in Figure 3.
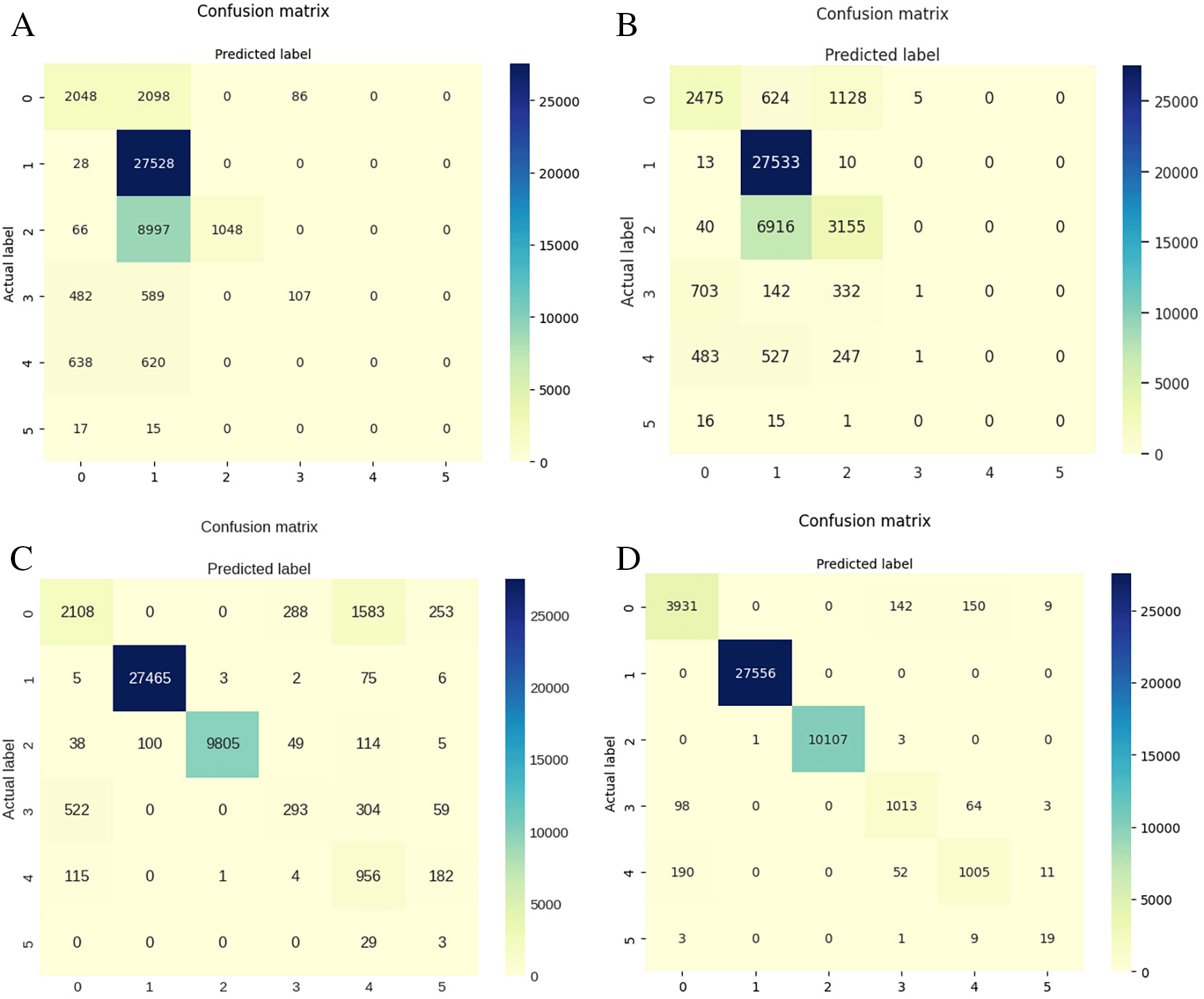
In addition to comparing and evaluating the performance of the ML algorithms deployed in this work, the authors also compared such algorithms with the existed related works, as shown in Table 3. In most of cases, the performance improvements have been achieved in the state-of-the-art even though there are different limitations and challenges that need further investigations in the domain area.
| Related works | Title of related work | Methods used | Performance % |
|---|---|---|---|
| 5 | Internet of Things Cyberattacks Detection Using Machine Learning | NB | 79% |
| 2 | Attack Detection in IoT Using Machine Learning | SVM, RF | 85.34% |
| 4 | Cyberattack Detection Using Machine Learning | KNN & RF | 88% |
| 7 | Attack and anomaly detection in IoT sensors in IoT sites using machine learning approaches | DT, RF & ANN | 99.4% |
| 10 | Botnet Attack Detection in IoT Using Machine Learning Technique | DT, LR | 94% |
| Our proposed work | Artificial intelligence model for internet of things attack detection using machine learning algorithms | DT, NB, SVM, LR | 98.34% |
IoT security attacks have been a hot issue in recent time. This paper aimed to design a multi-class IoT attack detection model using ML algorithms. The employed four supervised ML algorithms, namely; DT, SVM, LR, and NB were used to address the proposed problem related to identifying IoT attacks. The recent Canadian Institute of Cyber Security CICIoT2023 dataset, which contains the imbalanced instances and multi-class types of attacks with six classes, was used for designing and evaluating the proposed model. The dataset was splited into 80%:20% ratio for training and testing the model, respectively. The experiments are conducted using Python in Google Co-Lab.
To evaluate the model performance, we used tabular representation (accuracy) and confusion matrix for each employed algorithm. The prominent performance result has been found. In DT, we attained the maximum prediction accuracy rate of 98.34%. DT outperforms SVM at 91.5%, LR at 75%, and Bayes classifiers (NB) at 92%. Our model performs superior accuracy in the prediction of these IoT attacks when compared to other benchmarks of ML classification approaches.
In the area of IoT threat detection, our suggested model result offers several contributions, including resolving unbalanced data issues, enhancing detection precision, increasing imbalanced data awareness, improving performance, and forwarding future directions in the area. Therefore, the result could be enhancing security, reducing response time, and enabling adaptive defense to provide a significant contribution to the domain of IoT security. The work on IoT security attack identification using ML approaches holds great promise in improving IoT security.
However, there are different limitations faced in designing IoT security attacking systems. The first limitation was the dataset used could be too small or homogeneous for a reliable assessment and generalizability. The second limitation was the adversarial attacks that can manipulate IoT network traffic to evade or mislead ML based detection systems and can exploit vulnerabilities in the ML models themselves or manipulate the input data, making it difficult for the system to detect attacks accurately. The last but not the least limitation was only the ML algorithms have been employed in this work rather than deep learning algorithms that are important for performance improvements in large dataset.
Based on the limitations mentioned earlier, the improvement of the performance of IoT attack detection model using large datasets and the appropriate deep learning algorithms with their parameters will be our future consideration in the domain.
All necessary data available from Kaggle and download it after filling CIC DATASET DOWNLOAD FORM for “CIC_IOT_Dataset2023” form. https://www.unb.ca/cic/datasets/iotdataset-2023.html.
| Views | Downloads | |
|---|---|---|
| F1000Research | - | - |
|
PubMed Central
Data from PMC are received and updated monthly.
|
- | - |
Is the work clearly and accurately presented and does it cite the current literature?
Yes
Is the study design appropriate and is the work technically sound?
Yes
Are sufficient details of methods and analysis provided to allow replication by others?
Yes
If applicable, is the statistical analysis and its interpretation appropriate?
I cannot comment. A qualified statistician is required.
Are all the source data underlying the results available to ensure full reproducibility?
Partly
Are the conclusions drawn adequately supported by the results?
Yes
References
1. Radanliev P, Santos O, Brandon-Jones A: Capability hardware enhanced instructions and artificial intelligence bill of materials in trustworthy artificial intelligence systems: analyzing cybersecurity threats, exploits, and vulnerabilities in new software bills of materials with artificial intelligence. The Journal of Defense Modeling and Simulation: Applications, Methodology, Technology. 2024. Publisher Full TextCompeting Interests: No competing interests were disclosed.
Reviewer Expertise: AI security, IoT, cyber risk, blockchchain security, post-quantum cryptography.
Alongside their report, reviewers assign a status to the article:
| Invited Reviewers | |
|---|---|
| 1 | |
|
Version 1 25 Feb 25 |
read |
Provide sufficient details of any financial or non-financial competing interests to enable users to assess whether your comments might lead a reasonable person to question your impartiality. Consider the following examples, but note that this is not an exhaustive list:
Sign up for content alerts and receive a weekly or monthly email with all newly published articles
Already registered? Sign in
The email address should be the one you originally registered with F1000.
You registered with F1000 via Google, so we cannot reset your password.
To sign in, please click here.
If you still need help with your Google account password, please click here.
You registered with F1000 via Facebook, so we cannot reset your password.
To sign in, please click here.
If you still need help with your Facebook account password, please click here.
If your email address is registered with us, we will email you instructions to reset your password.
If you think you should have received this email but it has not arrived, please check your spam filters and/or contact for further assistance.
Comments on this article Comments (0)