Keywords
Organizational cybersecurity, Organizational immunity, General Directorate of Educational Planning
This article is included in the Fallujah Multidisciplinary Science and Innovation gateway.
This article is included in the Cybersecurity collection.
This research addressed organizational cybersecurity, which has emerged as a critical element in the digital age and has become a strategic issue for organizations working to protect user assets against security risks in the cyber environment. And Organizational immunity includes the policies and procedures adopted by an organization to protect its core values and correct performance deviations. The research purpose on studying the impact of organizational cybersecurity on organizational immunity at the Iraqi Ministry of Education/General Directorate of Educational Planning. There is a need to study this relationship to better understand how organizations can strengthen their capabilities in an advanced digital environment.
The research adopted a descriptive analytical approach, whereby 95 questionnaires were distributed and data was collected from 85 respondents, ready for statistical analysis. The data was analyzed using statistical tools (SPSS V.28&smartpls4) to verify the scale and analyze the relationships between variables.
indicate that the level of organizational cybersecurity implementation was first in relative importance, while organizational immunity came in second, and there is an impact relationship between organizational cybersecurity and organizational immunity, which reinforces the fundamental role of the General Directorate of Educational Planning in maintaining business continuity and limiting the impact of cyberattacks.
The research concludes that organizational cybersecurity plays an important role in enhancing organizational immunity, as the application of cybersecurity tools would enhance the role of the General Directorate of Educational Planning and its ability to withstand cyber threats, strengthen digital measures, improve protection, and ensure business continuity in the digital environment.
Organizational cybersecurity, Organizational immunity, General Directorate of Educational Planning
With the acceleration of the pace of technological development of information and the era of digitization of organizations and the transfer of many commercial and daily activities around the world via the Internet, the importance of cybersecurity has increased, as it has become an essential pillar to protect critical infrastructures and sensitive data, especially with the continuous spread of information breaches in both governmental and private institutions as well as the damage and sophisticated threats resulting from this in the cyber landscape, which requires institutions at different levels to develop strategies to mitigate threats, so it is necessary for institutions to build a model of cybersecurity culture to educate the From the above, A review of previous studies showed that most of them focused on the purely technical aspect of cybersecurity and rarely addressed the organizational aspect. Therefore, there is a need to fill the research gap by addressing the relationship between organizational cybersecurity and organizational immunity in government organizations, particularly in the education sector, through conducting an analytical study in the General Directorate of Educational Planning, which was chosen because it is a vital directorate in the Ministry of Education that relies on information systems used in administration, planning, and communications, which makes it vulnerable to cyber threats. In addition, it was found that there was no study that addressed the research variables in the Directorate of Educational Planning, which gives the research scientific, practical, and cognitive value.
The research was divided into several axes, as the first axis dealt with the methodological framework of the research, while the second axis reviewed the theoretical framework of organizational cybersecurity and organizational immunity, and the third axis focused on analyzing data and testing research hypotheses to reach results that clarify the impact of cybersecurity on organizational immunity in the Directorate of Educational Planning, and the research concluded by presenting the conclusions and recommendations of the research.
The diversity of digital systems and technological applications, as well as the use of artificial intelligence systems and advanced technologies in strategic decision-making, has posed a technological challenge for the General Directorate of Educational Planning to keep pace with these developments, in addition to its increasing needs to address security challenges that threaten the integrity of the Directorate’s data and information infrastructure. Therefore, the research problem emerged from the limited awareness and application of organizational cybersecurity technologies and their role in strengthening the organization’s immunity.
The main purpose of the research is to explain organizational cybersecurity and its impact on organizational immunity in the General Directorate of Educational Planning.
This might be accomplished by answering the subsequent inquiries:-
The importance lies in the following points:-
1- Its importance is highlighted by presenting a new model that takes into account the nature of the relationship between organizational cybersecurity and organizational immunity for the purpose of bridging the knowledge gap, with the aim of improving sustainable performance in government institutions, which in turn is reflected in their services.
2- The research contributes to enriching the scientific literature in the field of organizational cybersecurity and organizational immunity.
3- It benefits from the nature of the relationship between the research variables in providing decision-makers at the General Directorate of Educational Planning with actionable recommendations to raise the level of cybersecurity protection, reduce it, and address weaknesses in the cyber infrastructure.
The current research seeks to achieve the following:-
1- Measure the level of organizational cybersecurity and organizational immunity in the General Directorate of Educational Planning.
2- Analyze and test the statistical correlation between organizational cybersecurity and organizational immunity based on the specified indicators.
3- Presenting a set of practical findings and recommendations to enhance the level of organizational cybersecurity and immunity within the General Directorate of Educational Planning.
The research design reflects the research problem, objectives, and significance by revealing the relationship between two variables:
Organizational cybersecurity as an independent variable and organizational immunity as a dependent variable, as shown in Figure 1.
Ho.1: There is no significant impact of organizational cybersecurity on organizational immunity: -
Ho1.1: The first sub-hypothesis: There is no significant impact of training and organizational policies in organizational immunity.
Ho1.2: Second sub-hypothesis: There is no statistically significant impact of organizational effectiveness and government policies in organizational immunity.
Ho1.3: The third sub-hypothesis: There is no significant impact of the dimension of absorptive capacity in organizational immunity.
Ho.2: Second hypothesis: There is no significant Impact Organizational cybersecurity together in organizational immunity.
The research adopted a descriptive analytical approach and used a questionnaire as a data collection tool, which included 24 items reflecting the research variables (organizational cybersecurity and organizational immunity). In addition, it adopted measures from recent Arab and foreign sources, using a five-point Likert scale (strongly agree, agree, somewhat agree, disagree, strongly disagree). Table 1 illustrates Research terms and scale.
| Variables and dimensions of the study | Code | The number of questions | Scale source |
|---|---|---|---|
| Training and organizational policies | TAO | 4 | [1] |
| Organizational effectiveness and government policies | OEAGP | 4 | |
| Absorptive capacity | AC | 4 | |
| Organizational cybersecurity | OC | 12 | |
| Organizational learning | OL | 4 | [2] [3] |
| Organizational memory | OM | 4 | |
| Regulatory genes | RG | 4 | |
| Organizational immunity | OI | 12 |
The Ministry of Education/General Directorate of Educational Planning was selected as the field of application, and the research sample was a purposive stratified sample of directors and officials in the directorate. The statistical table Krejcie&Morgan4 was used to determine the sample size, as a simple random sampling method was adopted with a distribution of 95 questionnaires. Eighty-five questionnaires were valid for statistical analysis, representing 89% of the distributed questionnaires, which is a high and statistically acceptable percentage.
1- Organizational Cybersecurity Model
Figure 2 shows the questions of the dimensions of the organizational cybersecurity model, which consisted of three main dimensions (training and organizational policies, organizational effectiveness and governmental policies, and absorptive capacity). With a total of (12) questions, the table also showed the composite stability values (CR) for the dimensions of the organizational cybersecurity variable (0.898, 0.826, 0.831), which are within statistically acceptable limits (> 0.70), which indicates a high level of stability and confirms the quality of the scale, and the results showed that Cronbach’s alpha coefficient for the dimensions of the variable amounted to (0.833, 0.836, 0.896). (0.836, 0.896), which is higher than the accepted normative value (0.70), reflecting high internal consistency between paragraphs, in addition, the values of the average variance of the extract (AVE) for the organizational cybersecurity variable came within the acceptable range, reaching (0.564, 0.552, 0.690), exceeding the required minimum threshold (0.50). The results indicate that the sub-dimensions contribute significantly to explaining the total variance of the variable, which enhances the reliability of the model and its ability to explain the relationships between its components.
Table 2 shows the values of the estimates of the organizational cybersecurity model, where they ranged between (0.659-0.890), indicating that all paragraphs have a significant Impact on the dimensions of the model. The results of the (t) test also showed that the values ranged between (5.658-9.887), all of which are greater than the tabular value of (t) of (1.984) at the significance level (0.05). This reflects the high statistical reliability of the items and sufficient support for adopting the finalized model in subsequent statistical analysis.
2- Organizational immunity
As can be seen in Figure 3 which presents the questions of the dimensions of the organizational immunity model, namely (organizational learning, organizational memory, regulatory genes), with a total of (12) questions, and as shown in Table 3 the values of the composite stability coefficient (CR) for the dimensions of the organizational immunity variable (0.888, 0.890, 0.867), which are within the acceptable limits (> 0. 70). The results also showed that the values of Cronbach’s alpha coefficient for the same dimensions were (0.883, 0.892, 0.868), which also exceeds the accepted normative value (0.70), and indicates the existence of internal consistency between paragraphs, and the values of the average variance extracted (AVE) came within acceptable limits, amounting to (0.660, 0.670, 0.610), exceeding the required minimum threshold (0.50). These findings show that the sub-dimensions have a major role in understanding the organizational immunity variable’s overall variation as well as the model’s dependability and ability to effectively describe the relationships between its dimensions.
Table 3 showed the values of the estimates for the paragraphs of the organizational immunity model, which ranged between (0.691-0.913), indicating that all paragraphs have a significant Impact within the model. The (t) values, which ranged from (6.589-9.922), were all greater than the tabular value of (t) of (1.984) at a significance level of (0.05), which is a sufficient indicator for adopting the model in its final formulation in subsequent statistical analysis.
A set of statistical methods was adopted to provide statistical analysis of the research results and test its hypotheses. These methods included (confirmatory factor analysis, arithmetic mean, and standard deviation, coefficient of variation, relative importance, correlation coefficient, and linear regression analysis).
The phrase cybersecurity refers to a broader range of procedures and guidelines that shield computer networks and systems from threats and incursions of any kind in cyberspace.1 Cybersecurity is a very critical business challenge in the digital era and establishes effective policies for organizations to protect their assets and comply with regulatory mandates to enhance stakeholder confidence.5 Cybersecurity is also a critical element of an organization’s management that affects organizational strategies in a comprehensive ways.6 Integrating cybersecurity principles into organizational practices (OPs) improves organizational resilience by embedding security determinants into daily operations, and resource management empowers employees by prioritizing cybersecurity in their professional responsibilities.7 Additionally, studies reveal that a cybersecurity culture dramatically lowers the probability of successful cyberattacks. Employees who believe that cybersecurity is a significant part of the company culture are more likely to follow security procedures and feel more accountable for safeguarding the company’s resources.8
Cybersecurity is also known as the prevention of cybercrime, as the awareness of information security is playing a key role in preventing cybercrime.9 The concept of organizational cybersecurity may be defined as protecting computer systems from theft or corruption of their hardware, software or databases from disrupting the operations and services provided by the organization to the community.10 It is also known to be an external variable that may take into account directives that protect information technology and computer systems for the purpose of forcing companies to protect their systems and information from cyber threats and data breaches.11 According to Petrova et al.,Cyber security and information security are strongly related and overlap in some respects, but they are not the same, as information security is generally focusing on the protection of information and cyber security is one of its components, while cyber security focuses specifically on protecting information in cyberspace.12
When reviewing the literature related to the topic of organizational cybersecurity.
It was noted that there was a lack of clear guidance from researchers explaining the dimensions of this term. Therefore, we will rely on the dimensions identified by a study1:-
1- Cybersecurity training and organizational policies
Cybersecurity training is an indispensable aspect for employees, as it helps to ensure the security of the organization.13 Organizations need cybersecurity training and Awareness with a focus on teaching employees to act according to certain IT security principles and objectives.14 Cybersecurity awareness training includes implementing regular training sessions to teach employees about the latest cybersecurity threats, best practices, and the organization’s policies and procedures.15 Fostering a culture of knowledge sharing among employees coupled with training can improve organizational resilience against security vulnerabilities.16 Good security-related policies promote a more cohesive and standardized approach to cybersecurity within organizations.17 It is essential for HR departments to include training as an essential part of employee onboarding in order to ensure an adequate level of competence in dealing with threats and incidents.18 Regular training sessions and awareness programs enable employees to recognize potential threats, adhere to security policies, and adopt safe behaviors in their daily work routine.19
In addition, policies in the field of cybersecurity constitute a set of legislation, programs and procedures formulated by a governing body within the organization, and these policies serve as regulatory frameworks that define protocols and standards to be followed to protect information and physical assets from potential threats, and policies are necessary to strengthen cyber defenses and mitigate vulnerabilities and potential attacks in the digital domain.20 A cybersecurity policy has a positive impact on employees’ beliefs and behavior directed towards cybersecurity.21 Developing a comprehensive cybersecurity policy is a strategic answer to protect organizational data and information, and it establishes a framework for employees to follow security measures and enforce compliance with cybersecurity standards.22
2- Organizational Effectiveness and Government Policies
In the age of rapid digitization of organizations, cybersecurity has emerged as an integral part of organizational safety and effectiveness, which includes not only maintaining the confidentiality, integrity, and availability of digital assets but also establishing an organizational cybersecurity culture and thus human behavior.23 Cybersecurity has become an essential pillar for protecting infrastructure, sensitive data, and individual privacy.24
The capacity of organizations to deal with cybersecurity can be enhanced by complying with standards, laws, and government regulations that can enhance an organization’s ability to defend against cyberattacks.18 The governments around the world have also recognized the need for formal regulations to protect sensitive data and critical infrastructure.25 Government policy is the result of a set of activities that operate within an environment where government policy makers determine what to do and what not to do, and addressing issues related to cybercrime and threats is a priority for every government.26
3- Absorptive Capacity
The theory of absorptive capacity was developed by Cohen and Levinthal (1990) to explain the structural readiness and ability of organizations to engage in new ideas and recognize the value of improvements and innovation.27 According to Cohen, an organization’s ability to stay competitive in quickly changing industries depends on its ability to absorb and acquire new knowledge. Businesses with high absorptive capacity are also better equipped to comprehend and react to environmental issues and changes in the market and environment, which makes their operations flexible and sustainable.28 Absorptive capacity supports an organization’s development of learning. Companies that excel in absorptive capacity create an environment where continuous learning and knowledge sharing are embedded in the organizational culture.29 Cohen and Leventhal define the term “absorptive capacity” as an organization’s capacity to gather, assimilate, and apply fresh outside information to give the business a competitive edge30–32 and Zahra and George (2002) defined it as a set of routine organizational procedures and processes through which organizations acquire, absorb, transform and apply knowledge to produce dynamic organizational capacity.33,34 Kim defined it as the ability to learn and solve problems.35 It also refers to an organization’s ability to absorb, learn, integrate and assimilate external knowledge within the organizational context.36
Dejos (1997) was the first to introduce the term organizational immunity systems in the business management literature, as he mentioned it in a narrow context in which he discussed the concept of organizational culture, calling for the need to deal with organizations as a living organism that can adapt and interact with the surrounding environment and overcome its threats so that it can survive.37 Management scholars also use this medical term in organizations because the organization is similar to a living organism, and it has been defined as a social entity whose main purpose is to form a defensive system for the organization to face the risks that may threaten its survival or affect its work.38 The immune system in organizations is considered a vital device that works to counter any harmful influences that try to create negative influences and disturbances that lead to the deviation of the organization’s path from its desired goals.39 Organizational immunity is defined as the ability to protect and defend itself, either by preventing or overcoming weaknesses and threats or by removing them, avoiding them, preventing their growth or stopping their effects.40 It may also be described as an integrated work system that seeks to utilize the resources at hand in order to preserve the organization’s stability and safeguard it against dangers.2 It Refers Majeed & Lafta a collection of regulations, guidelines, and policies that rely on a collection of people and procedures to create a wall that keeps the company from straying from the course necessary to accomplish its objectives, regardless of whether the departure is due to internal or external factors.41
The dimensions of organizational immunity were determined according to the study Refs. 2 & 3:-
1- Organizational learning: It is a multidimensional latent construct that includes managerial commitment, systems perspective, openness, experimentation, knowledge transfer and integration.42 It refers to the organizational capacity to learn the attributes, practices and issues within the organization that facilitate learning processes, including generating, acquiring, disseminating and integrating knowledge and modifying behaviors to reflect new cognitive insights to improve performance.43 Organizational learning refers to the process by which an organization or group of professionals collectively acquire, share, and apply knowledge to improve its performance and adapt to changing circumstances.44
2- Organizational memory: It is the means by which knowledge from the past is brought into current organizational activities and provides the knowledge needed to perform the current functions of the organization.45 It is an appropriate metaphor that can be used to define the knowledge and information that an organization possesses and the processes it uses to store and retrieve it when needed.3 It is defined as the process by which data or information that is stored is processed through various mechanisms related to this process.46
3- Regulatory genes: is a modern management technique that analyzes the internal characteristics of organizations based on the principle that every organization is like a living organism, with genetic traits that distinguish it from other organizations. The term “organizational DNA” was coined by Booz Hamilton, which sought to provide organizations with an easy and accessible way to identify and address the problems and difficulties that hinder and affect their success.47 Organizational DNA has an effective role in defining organizations and leading management functions such as decisions, organizational structure, teamwork and communication.48 Organizational DNA is regarded as one of the most important aspects of management since it influences employee behavior and, consequently, the organization’s performance. It also helps to identify the organization’s strengths and weaknesses, forecast employee behavior and performance, and develop work expectations that inform institutional and individual decisions and ensure the organization’s sustainability.49
Effective cybersecurity management enhances business operations and enables companies to turn cybersecurity into a competitive advantage by adopting proactive cybersecurity measures that not only protect assets but also assure business partners and customers of the company’s commitment to security. This can lead to smoother business transactions and partnerships and enhance trust across business networks.23 The importance of cybersecurity has been highlighted by the increasing frequency and severity of cyberattacks, especially since the financial impact of these breaches is significant, with costs extending beyond immediate damages to include long-term effects such as loss of business, legal fees, and regulatory fines.50 In addition, the role of organizational cybersecurity is not limited to protecting information systems, but also enhances their ability to adapt and withstand risks, thereby strengthening the organization’s immunity. Ali, points out that the organizational immune system consists of people, policies, procedures, processes, culture, and modern and sophisticated systems and mechanisms that act as a strong barrier to counter external threats and address weaknesses within the organization, through which the organization maintains its integrity in an environment fraught with potential consequences.37
From the above, organizational cybersecurity provides a line of defense that reduces information leaks and impacts on operational processes; thereby creating an environment that is responsive to potential risks and promotes a culture of organizational immunity. On the other hand, organizational immunity increases the efficiency of organizational cybersecurity by providing a flexible management framework to accommodate technological developments and continuously update them. Thus, the relationship between the two is complementary, organizational cybersecurity enhances the organization’s ability to face risks and threats, and organizational immunity provides the necessary administrative support through planning and continuous improvement, thereby reducing operational losses and increasing the organization’s efficiency.
The study reviews the statistical analysis data to describe the research variables as follows:-
Descriptive analysis and interpretation of the sample respondents’ answers to the organizational cybersecurity and organizational immunity statements are presented in this study as follows:-
A- Descriptive analysis of Organizational Cybersecurity:-
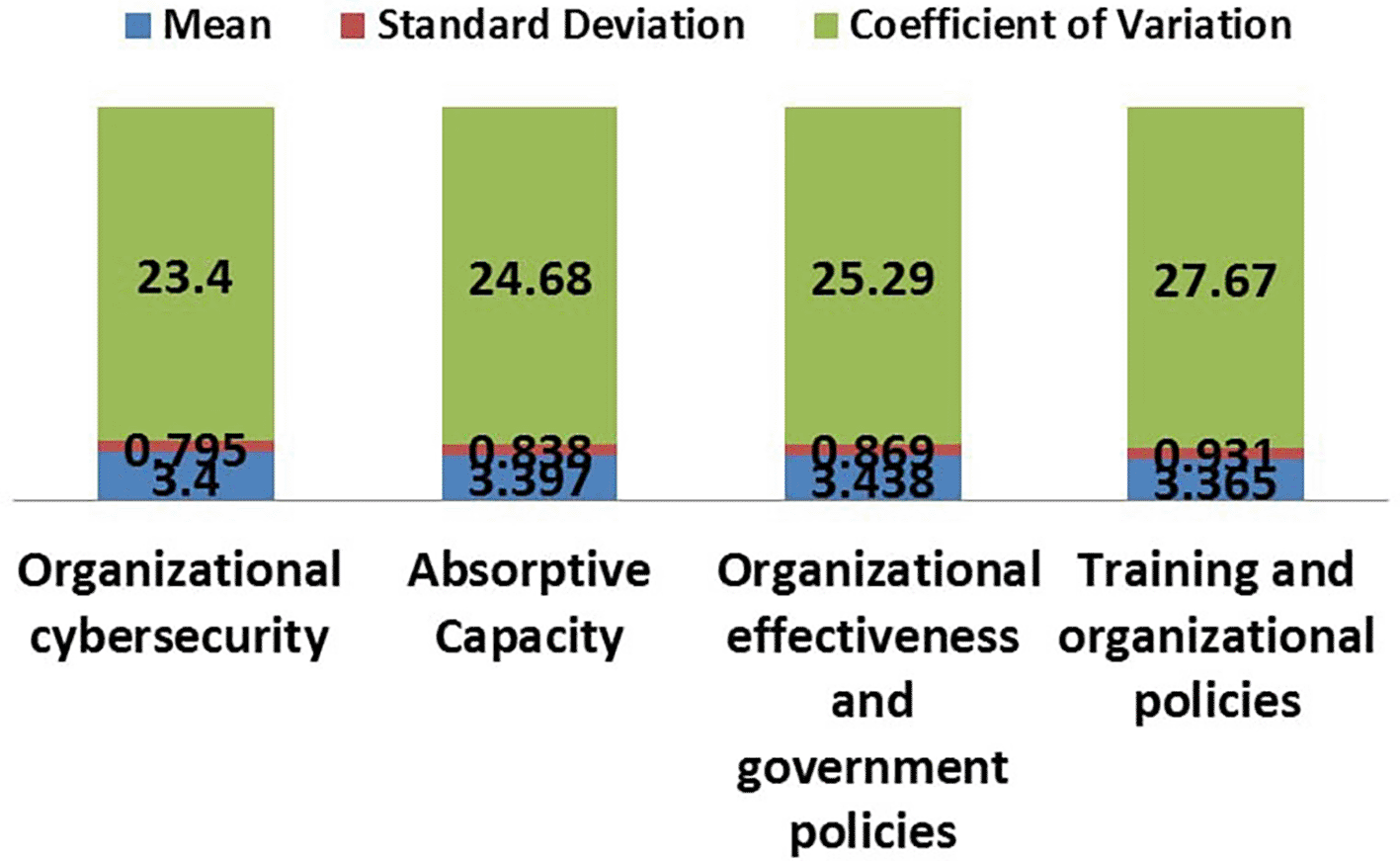
Table 4 indicates and Figure 4 the results of a descriptive analysis of the dimensions of organizational cybersecurity, as the arithmetic mean of the dimension of training and organizational policies (3.365) with standard deviation (0.931) and a coefficient of variation (27.67%),which indicates relative stability in the responses of the sample towards this dimension, ranking third in relative importance, This dimension needs to be developed along with clear and strengthened training policies, while the dimension of organizational effectiveness and government policies, recorded an arithmetic mean (3.438) and a standard deviation (0.869) and a coefficient of variation (25.29%), ranking second in relative importance. While the absorptive capacity dimension recorded a mean of (3.397), standard deviation (0.838) and coefficient of variation (24.68%), ranking first among the dimensions in terms of relative importance. The organizational cybersecurity dimension achieved the highest level of stability in the sample responses with an arithmetic mean of (3.400), standard deviation (0.795) and coefficient of variation (23.40%), ranking first among the dimensions by relative importance which reflects a high perception of the importance of this dimension.
B- Descriptive analysis of Organizational immunity
Table 4 shows and Figure 5 the descriptive results of the dimensions of the organizational immunity variable, as the organizational learning dimension came with an arithmetic mean of (3.238), standard deviation (0.948) and coefficient of variation (29.27%), ranking third in relative importance, which reflects a relatively moderate response by the sample towards this dimension. Therefore, the Directorate should enhance institutional learning and continuous professional development programs. while the organizational memory dimension recorded an arithmetic mean of (3.306), standard deviation (0.955) and coefficient of variation (28.88%), ranking second in relative importance, indicating an advanced perception of the importance of this dimension, while the dimension of regulatory genes achieved the highest arithmetic mean of (3.462) with standard deviation (0.864) and coefficient of variation (24.95%). This indicates a higher stability of the sample’s responses, which qualified it to occupy the first place in relative importance, This means that the directorate has a work culture and values regarding employee behavior., and considering the organizational immunity variable as a whole, it recorded an arithmetic mean of (3.335), standard deviation (0.861) and coefficient of variation (25.82%), ranking second in the overall ranking of the studied dimensions, an indicator of the sample’s advanced awareness of the importance of this variable in the organizational work environment.
The study presents the findings from the statistical examination of the research hypotheses in the following manner:-
1- Testing the first main hypothesis:
(There is no a Significant Impact of Organizational Cybersecurity on Organizational Immunity).
Table 5 shows and Figure 6 that the relationship between organizational cybersecurity and organizational immunity was strong and statistically significant, as the correlation coefficient (R) between them reached (0.886), This means that increased organizational cybersecurity is linked to increased immunity within the directorate, which is a high value indicating a strong positive correlation between the two variables, and the value of the coefficient of determination (R2) of (0.785) showed that organizational cybersecurity explains 78.5% of the total variance in organizational immunity, This indicates that organizational cybersecurity is not merely a preventive or technical measure, but rather a crucial element in enhancing the capabilities of the General Directorate of Educational Planning, in addition, the adjusted (R2 Adj) value amounted to (0.782), which reflects the stability of the model when generalizing the results to the statistical community, while the (F) test recorded a value of (303.081), which is significantly greater than the tabular value of (F) at the significance level (0.05), with a significant value (Sig = 0.000), which indicates the significance of the model as a whole, the results also showed that the calculated (t) value for the organizational cybersecurity variable was (17.409), which is greater than the tabular value of (t) of (1.984) at the level of significance. level (0.05), and the value of the regression coefficient (β) indicates that increasing organizational cybersecurity by one unit leads to an increase in organizational immunity by (95%), reflecting a strong and direct impact of the independent variable on the dependent variable.
2- Examining the sub-hypotheses of the organizational cybersecurity dimensions in relation to organizational immunity, as indicated by Table 6:-
The Table 7 showed the results of the regression analysis between the dimensions of organizational cybersecurity in the organizational immunity variable, where the results revealed that there are significant and statistically significant impact for all dimensions.
| Independent variable | (t) | R | (R2) | (R2) Adj | (F) | Sig | Dependent variable | ||
|---|---|---|---|---|---|---|---|---|---|
| organizational cybersecurity | (α) | 0.074 | 0.387 | 0.886 | 0.785 | 0.782 | 303.081 | 0.000 | organizational immunity |
| (β) | 0.950 | 17.409 | |||||||
(There is no a significant impact of organizational cybersecurity on organizational immunity)
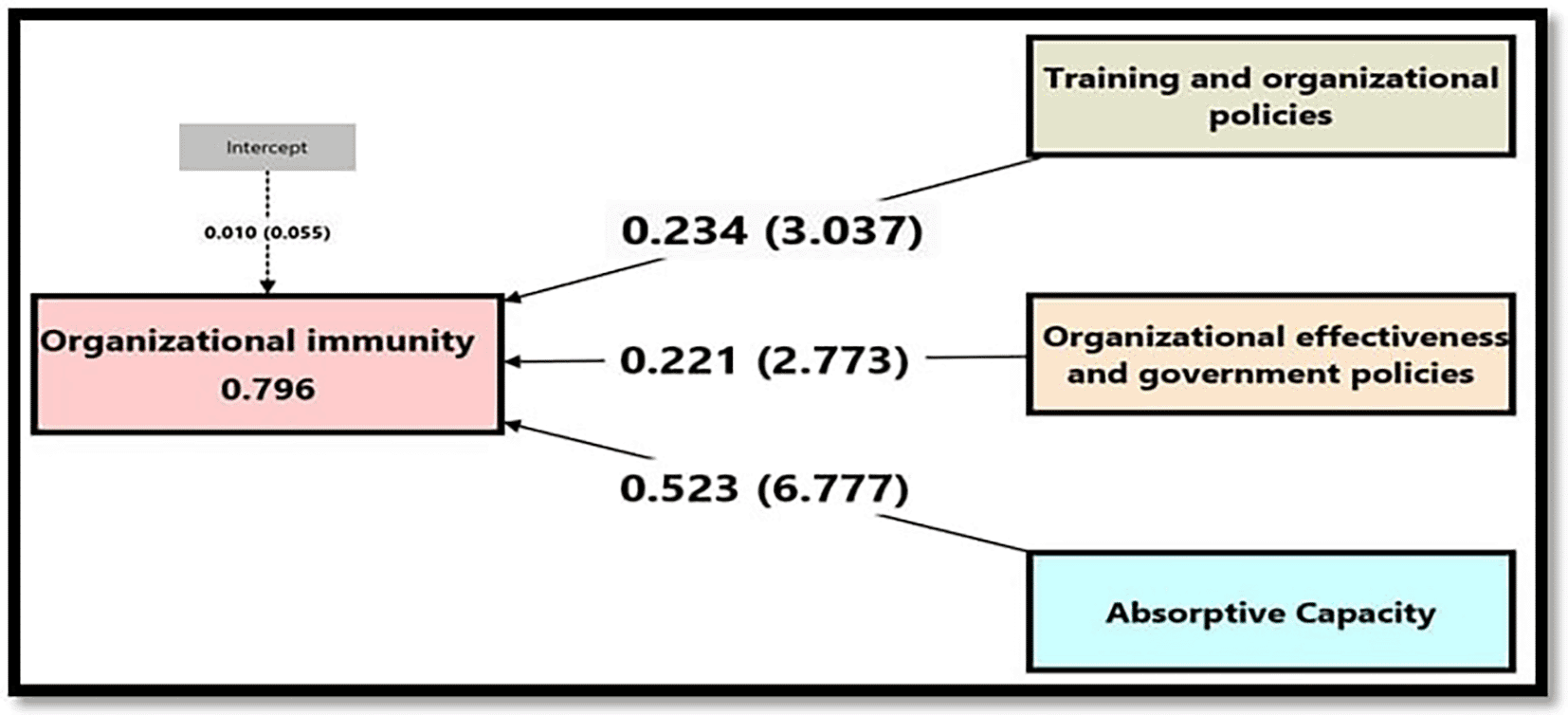
Table 8 and Figure 7 indicate the results of the impact analysis between the dimensions of organizational cybersecurity on organizational immunity, as the extracted F value achieved a value of (110.021) indicating that there is a significant impact between organizational cybersecurity on organizational immunity, This indicates the acceptance of the alternative hypothesis (there is a significant impact of organizational cybersecurity on organizational immunity),According to the R2 value (Adj) shows that the dimensions of organizational cybersecurity together were able to explain 79% of the changes in organizational immunity, The extracted (t) value of (3.037, 2.773, and 6.777), respectively, is greater than the tabulated (t) value of (1.984) and indicates that the impact of the parameter (β) for the dimensions (training and organizational policies, organizational effectiveness and government policies, absorptive capacity), is real as increasing the impact by one unit will increase organizational immunity by (23%, 22%, and 52%) respectively, As for the impact of the absorptive capacity dimension, the results showed that it has no significant impact on organizational immunity.
As evidenced by the results of the multicollinearity test between organizational cybersecurity dimensions, the Tolerance values ranged between (0.350-0.431),They are all higher than the minimum acceptable threshold of (0.10), indicating that there is no serious issue of multicollinearity. As for the VIF values, they ranged between (2.320-2.861), which are all much lower than the recommended upper limit of (5), which reinforces the previous result and confirms that there is no issue of multicollinearity between the independent variables in the model.
In reviewing the research results, it was found that the organizational cybersecurity variable plays an important role in enhancing the organization’s immunity, especially in the work environment of the General Directorate of Educational Planning, as the high level of employee awareness will contribute to reducing cyber risks and threats and enhance business continuity and maintain the reliability of the Directorate’s systems and data. The results also showed that organizational cybersecurity has a significant impact on organizational immunity, rejecting the null hypothesis and accepting the first alternative hypothesis, as well as accepting the second alternative hypothesis that there is a significant impact between organizational cybersecurity and organizational immunity.
Therefore, the Directorate of Educational Planning must pay attention to the results, considering that organizational cybersecurity is an important technical element that contributes to building sustainable organizational immunity capable of responding efficiently to crises and threats.
1- According to statistical data, the organizational cybersecurity variable’s dimensions had high stability coefficient values, and the organizational immunity scale’s dimensions also demonstrated stability, indicating the scale’s quality. As a result, the model is thought to be more trustworthy when describing how organizational immunity and cybersecurity are related.
2- When the organizational cybersecurity variable was descriptively analyzed, the mean result was (3.400) and came in first place in terms of relative importance, in terms of relative importance, while the organizational immunity variable achieved a mean of 3.335, ranking second in terms of relative importance, which indicates that there is good awareness and interest in the importance of these variables in improving, sustaining, and enhancing outstanding performance.
3- The research revealed that the correlation between organizational cybersecurity and organizational immunity was strong and statistically significant in the General Directorate of Educational Planning, confirming that digital practices directly contribute to enhancing its ability to cope with crises and difficulties in the organizational work environment.
4- There is impact between organizational cybersecurity and organizational immunity. The results also show that the dimension of “absorptive capacity” has no significant Impact on organizational immunity, which reinforces the essential role of the General Directorate of Educational Planning in maintaining business continuity and minimizing the impact of cyber-attacks.
1- The necessity for the Ministry of Education/General Directorate of Educational Planning to create cybersecurity policies and procedures that adhere to the most recent global standards for safeguarding digital infrastructure.
2- Work on training employees and organizing courses for them on technology to raise awareness of cyber threats and how to deal with them, which contributes to strengthening the organizational immunity of the General Directorate of Educational Planning.
3- Allocate adequate budgets to invest in cybersecurity infrastructure, including network protection devices, secure and advanced cloud solutions, and protection software to prevent any breaches that threaten its operating systems.
4- The need to integrate the organizational cybersecurity policy into the strategic planning of the General Directorate of Educational Planning and consider it a key part of governance and organizational prevention, as well as establishing partnerships with institutions specializing in cybersecurity to benefit from their expertise and information.
5- Conducting more future studies on organizational cybersecurity and organizational immunity in other health, industrial, and commercial institutions and comparing them with the results of the current research.
The research was performed based on the ethical guidelines in the Ministry of Education Iraqi, which does not ethical require formal approval for social science studies that do not involve medical matters, personally identifiable information, or sensitive data. The Ministry does not have an Institutional Review Board for this type of research; therefore, no formal ethical approval or exemption was required, however, all ethical principles were adhered to.
All participants in the research were informed of the purpose of their voluntary participation and the confidentiality of their responses, which were used for research purposes. All participants were adults and gave their informed consent verbally. The research used an anonymous questionnaire and did not collect any information that could identify them. In addition, written consent was not required for low-risk research.
All research data are available under the terms of the Creative Commons Attribution 4.0 International license (CC-BY 4.0) at: https://doi.org/10.5281/zenodo.17924397.51
The questionnaire used in this research is available file on the Zenodo platform at the following link: https://doi.org/10.5281/zenodo.17924397.51 And may be reused under an open and free license.
| Views | Downloads | |
|---|---|---|
| F1000Research | - | - |
|
PubMed Central
Data from PMC are received and updated monthly.
|
- | - |
Provide sufficient details of any financial or non-financial competing interests to enable users to assess whether your comments might lead a reasonable person to question your impartiality. Consider the following examples, but note that this is not an exhaustive list:
Sign up for content alerts and receive a weekly or monthly email with all newly published articles
Already registered? Sign in
The email address should be the one you originally registered with F1000.
You registered with F1000 via Google, so we cannot reset your password.
To sign in, please click here.
If you still need help with your Google account password, please click here.
You registered with F1000 via Facebook, so we cannot reset your password.
To sign in, please click here.
If you still need help with your Facebook account password, please click here.
If your email address is registered with us, we will email you instructions to reset your password.
If you think you should have received this email but it has not arrived, please check your spam filters and/or contact for further assistance.
Comments on this article Comments (0)