Keywords
Clifford operator, quantum permutation pad, quantum communication, quantum network, security, confidentiality, encryption.
This article is included in the Cybersecurity collection.
This article is included in the Quantum Technology collection.
Clifford operator, quantum permutation pad, quantum communication, quantum network, security, confidentiality, encryption.
Classical communications and networks, such as sonars, cellular networks, and the Internet, use the macroscopic properties of acoustic, electromagnetic, or light waves. In contrast, quantum communications use the microscopic properties of light. For instance, using an appropriate encoding, the quanta of light, called a photon, is used for quantum data communications. Each photon represents a quantum value. Applications of quantum communications include secret communications, quantum networking, and distributed quantum computing. Quantum networks are envisioned for quantum communications across long distances. A quantum network comprises links, repeaters, routers, and terminals. Nodes combine classical memory and quantum bit (qubit) memory. They have classical and quantum computing capabilities. Links are the communication channels, which may be classical or quantum. Applications of quantum networks encompass communications and computation. Quantum communications and networking enable the transfer of quantum states from one location to another. They permit pooling quantum computation resources to solve complex and distributed computing issues.
As with classical data, quantum data is vulnerable to various attacks.1–6 Quantum data needs to be protected. Fundamental properties are authenticity, confidentiality, integrity, and replay protection.7–9 We focus on the authenticity, confidentiality, integrity, and replay protection of quantum messages. An authenticity attack deceives the destination about the trustworthy source of a message.7,9 Mitigating the authenticity attack requires a proof of the source identity in a message. Confidentiality protection mitigates the risk of disclosing or leaking information contained in messages. Confidentiality protection is achieved by ciphering plaintext messages. An integrity attack modifies the content of a message. In the quantum setting, this modification on a quantum state takes the form of a unitary transformation . The state is modified by . Mitigating this attack requires a modification detection mechanism. In the quantum setting, a replay attack in the classical sense is not possible because of its non-cloning property. However, an adversary can delay the delivery of a message or, when it knows how, can recreate the state. Mitigating this attack requires a mechanism to ensure that a message is new. Classical computing uses a digital signature to address authenticity, integrity, and replay attacks, possibly combined with a nonce field or a timestamp. This signature mechanism cannot be used in the quantum world in the classical sense.7 Indeed, generating a digital signature in the classical sense requires reading the message content and generating a corresponding signature value using, for instance, a one-way hash function. Reading the content of a quantum state, i.e., measuring, is destructive. However, in the following, we use the signature concept with the understanding that it is not obtained by calculating a value that involves measuring the content of a quantum message.
The article includes one main result. It presents a quantum data protection scheme that achieves all these properties, acknowledging that, at least in the short term, qubit bandwidth is narrow. Such protection schemes need to be lightweight (few additional qubits are required to implement a security scheme). The solution integrates two existing cryptographic schemes: Clifford-operator based authentication9 and quantum permutation pad (QPP).10 In this context, lightweight means that few additional qubits are required to implement a security scheme. Confidentiality is achieved using quantum permutations while authenticity, integrity, and replay protection are obtained using quantum Clifford operators. While this new protection scheme benefits from the security analyses developed for the two cryptographic schemes that it uses, the article takes the investigation further by combining a collision probability analysis, Clifford-operator-based authentication, the QPP symmetric-key encryption, and the block counter mode to create a quantum data protection scheme.
We review related work and introduce relevant quantum information background. We present and analyze the original quantum data block cipher and authentication scheme.
The work presented in this article is about protecting quantum data using quantum resources. It is a topic that has received attention in the research literature, as discussed in this section. Work can be categorized into two groups: authentication and confidentiality.
Barnum et al. introduced an authentication scheme for quantum data, considering their specific nature, and defined the concepts of completeness and soundness in this context.7 Foundations for cryptographic schemes for authentication have been proposed by Aharonov et al.11 and Broadbent and Wainewright,12,13 building on quantum Clifford operators. This work has been used to build an authenticity, integrity, and replay protection scheme for quantum messages by Barbeau et al.,14,15 with demonstrated soundness and completeness, and to analyze attack probability. Other quantum data authentication efforts include the work of Das and Siopsis,16 building on a position authentication protocol, and Satoh et al.,17 building on the concept of quantum state tomography.
For confidentiality, asymmetric and symmetric encryption schemes have been proposed by Alagic et al.18 and St-Jules,19 using Clifford operators. Efforts have been devoted to adapting the Advanced Encryption Standard (AES)20 to the quantum environment.21–23 A challenge is the amount of required quantum resources. In the short term, the available quantum computers have low quantities of memory and high error probabilities in comparison to classical computers. New lighter-weight quantum encryption schemes requiring fewer quantum resources have been proposed.24–26 Kuang and Barbeau introduced a universal symmetric encryption scheme called QPP.10 The scheme can be used in several ways in classical and quantum environments.
In this article, we propose and analyze a symmetric key encryption scheme for blocks of quantum data. Building on our previous research,9,10 a general symmetric-key cipher is developed building on QPP in counter mode. Conditions are identified to achieve perfect indistinguishability. Use cases are also identified where perfect indistinguishability is not achieved, but where the probability of collision is low. As emphasized in,10 the QPP scheme can be considered for both classical data and quantum data. In companion papers, we developed a QPP block cipher scheme in counter mode for classical data adapted specifically for the underwater environment.14,15 For the encryption aspect, this article parallels this work for quantum data for a general quantum networking environment. More related work is cited in the following sections.
In the quantum computing model, the unit of information is called the quantum bit (qubit). Mathematically, using the Dirac ket notation , the Boolean values zero and one are represented, with the matrix-form equivalent, as
Ket zero, i.e., , and ket one, i.e., , are the standard computational basis states. A qubit can be in both states and at the same time. A qubit is in a continuum of intermediate states. These intermediate states are called a superposition. A superposition is represented as a unit vector in a complex vector space. Let and be two complex numbers, with the constraint that [1]
The term reads as ket . The factors and are the probability amplitudes associated with each state, i.e., and . In other words, we do not know in which state a qubit is. According to the probabilistic model of Equation (3), however, the actual measurement of a qubit yields , i.e., Boolean value zero, with probability and , i.e., Boolean value one, with probability . The matrix format is a convenient alternative equivalent representation of the linear superposition of a qubit:
The two coefficients and are organized in a one-column, two-row vector. A qubit state that can be written in the form of Equation (4), that is, in the column-vector form, is called a pure state. A qubit is a two-dimensional entity. Using probability amplitude , the first dimension defines the 0 information component. Using probability amplitude , the second dimension defines the 1 information component.
Qubits can be composed together. For instance, a two-qubit register consists of a superposition of the four states , , , and , i.e., the four possible two-bit binary values. Together with the corresponding probability amplitudes , , , and , the two-qubit linear superposition is
All , , , and are complex numbers with the constraint that is equal to one.
In general, a -qubit quantum register is a -term expression of the following form
The computational basis is the orthogonal basis
A -qubit quantum register is a -dimensional entity. The th dimension, using probability amplitude , defines the th information component, with . Both the summation form and equivalent column-vector form are shown. In the summation form, the plus sign is conjunctive, rather than disjunctive. In the quantum-superposition model, all terms in the summation exist simultaneously. One can also appreciate the memory complexity of simulating the quantum computing model with a classical one. A -qubit register requires the storage of probability amplitudes. For instance, the memory complexity of a 10-qubit register is in the order of kilobytes, a 20-qubit register is in the order of megabytes, and a 30-qubit register is in the order of gigabytes.
The probability amplitudes are organized in a one-column, -row vector in the column-vector form. The ket notation reflects the vectorial nature of a qubit or a quantum register. The term ket can be interpreted as a mapping to a column vector of the corresponding probability amplitudes:
We first briefly review the highlights of Clifford-operator-based authentication, QPP encryption, and the block counter mode. Then, we define original source and destination algorithms for authenticated and confidential quantum data communications.
The following four matrices constitute the Pauli operators:
Over the -qubit quantum states, the Pauli matrices are the set of all by matrices resulting from tensor products like , where are Pauli operators. The set has . Pauli matrices form a group. Hence, they can be interpreted as operators mapping Pauli matrices to Pauli matrices.
The set contains all the Pauli matrices in excluding the identity matrix . The set represents the set of all complex numbers modulo one. That is, is equal to , with equal to . The set represents all the by unitary matrices. Given a unitary , its conjugate transpose , and a Pauli matrix , the expression is the conjugation of matrix by unitary .
Over the -qubit quantum states, the set of Clifford operators is defined as
A Clifford operator is a bijection mapping Pauli matrices in to Pauli matrices in , through the action of conjugation. The suffix implies that two Clifford operators, different solely because of a factor in , are considered equivalent. The set has elements. In the following, we refer to it as .
Let us consider the -qubit orthonormal computational basis defined in Equation (6). Let be the vector space where every element of it can be expressed as a linear combination of members of this basis. The elements of the symmetric group are permutations over the set . The degree of the group is . It is of order . This means that there are permutation operators. In the following, we refer to them as . Each of them can be represented by a by matrix , where . Note that every permutation is a bijective function from the set to itself. Furthermore, the inverse of , denoted as , is also contained in the symmetric group .
A plaintext is made of vectors in . QPP encryption of plaintext uses a sequence of randomly selected permutations corresponding to the list , all selected in group . The sequence is the encryption key of message . The encryption of plaintext message with key is denoted as . It corresponds to the sequence of vectors where . Conversely, the decryption of , encrypted with key , is denoted as . It corresponds to the sequence of vectors , .
(Shannon perfect secrecy). For any pair of plaintexts and , when ciphertext is equally likely to be the encryption of or , the corresponding cryptographic scheme is perfectly secure.
The QPP cryptographic scheme is perfectly secure.
Proofs can be found in Refs. 10 and 14. The proofs establish that the probabilities are identical for all messages. The statement of Theorem 1 is theoretical because it requires very long keys. In the following, we use the QPP practically. This property is not maintained.
The implementation of QPP for quantum data has been investigated by Kuang and Perepechaenko.27–29 They proposed solutions to several quantum implementation issues, while the open problem of dispatching quantum permutations - that is, the selection of the applied permutations in a quantum circuit - is highlighted. The security of block sizes () two, three, four, and five is analyzed for the number of different permutations in a session required to achieve 256-bit of entropy, to mitigate the risk of breaking keys by the Grover’s algorithm.30–32 It is highlighted that a 256-bit size yields a brute force search space of keys. In the sequel, we take the security analysis one step further. As highlighted by Bellare and Rogaway, making the plaintext hard to recover from ciphertext is not enough to declare a cryptographic scheme secure.33 Indeed, information may leak just by observing patterns in traffic. In the next section, we analyze the probability of collisions, which is a cause of information leakage.
The concept of block counter mode has been examined in detail by Bellare and Rogaway.33 We summarize the main facts.
There are four main block modes, namely the electronic code book (ECB), cipher-block chaining (CBC) with a random initialization vector (IV), counter-based version of CBC (CBCC), and counter (CTR). The block modes are compared in Table 1. An important criterion is the risk of information leakage, which is significant for both the ECB and CBC with random IV modes. We use the CTR mode because of the low risk of information leakage.
The symmetric key block cipher with authentication is described hereafter. Let and be non-null positive integers. A quantum plaintext message consists of quantum blocks . Each block consists of qubits. An additional qubits are added to every block for a signature field; is a non-null positive integer.
There are two participants: a message source and a message destination. They share the following security parameters: i) block size (), ii) number of blocks in a message (), iii) length of the signature field (), iv) a set of Clifford operators randomly selected in , and v) a set of permutations randomly selected in . and are non-null positive integers. The source and destination share two secret arbitrary long sequences of random numbers , modulo , and , modulo . The sequence and set , and the sequence and set can be interpreted as the session authentication and encryption keys shared between the source and destination.
Before transmission, the source signs and encrypts each message. On the source side, there is a static variable . It is initialized to zero. After the completion of the encryption of a message, the new value of the static variable is incremented by units.
The plaintext is signed with a sequence of randomly selected Clifford operators:
All operators are in the set . The selection of Clifford operators is determined by the sequence of random numbers . The message signing key is the sequence of Clifford operators .
Following the signature procedure, the signed plaintext is encrypted with a sequence of randomly selected permutations:
All permutations are in the set . The selection of permutations is determined by the sequence of random numbers . The message encryption key is the sequence of permutations .
The quantum ciphertext and the value of classical variable are sent together to the destination.
Note that the term signature is used but not in the classical sense. A classical message signature is calculated by reading the payload of a message. For quantum data, reading the payload to calculate a signature is not feasible because the measurement of the payload qubits would destroy their states.
It is assumed that the plaintext is random and unbiased. A diffusion phase before encryption, on the source side, and an assembly phase after decryption, on the destination side, can be added to remove statistical bias in ciphertext. See Ref. 27 for a circuit design which does that using CNOT gates.
Building the set of Clifford operators involves the random selection of integers in the range one to and mapping these integers to Clifford operators. Koenig and Smolin have published a algorithm for doing this mapping while van den Berg34 proposed a algorithm. Barbeau et al.9 investigated this aspect for message key purposes.
The destination receives a quantum ciphertext and a classical value . For the purposes of replay protection, the destination ensures that the value of is new. The ciphertext consists of blocks of qubits , . The decryption of a block with index consists of the following product:
is the conjugate transpose of Clifford operator . The product is an identity. is the inverse permutation of . The product is also an identity. Assuming that a received message is intact, we have:
The original content is restored. To confirm that a verification is performed, measuring the qubits from positions to of every block, testing equality with the corresponding block number , and taking the logical conjunction of the results:
The result is the Boolean value . When it evaluates to one, the message is accepted and the resulting plaintext is
Otherwise, the ciphertext is rejected.
The message verification key is the sequence of conjugate transposes , which can easily be derived given . Verification of the condition of Equation (16) is interpreted as a proof of ownership of the authentication key by the message source and a validation of integrity. The value of the signature suffix aims to make every message unique, for replay protection. However, there is a risk of collision according to the selected security parameters. The collision probability is further investigated in the next section. The message decryption key is the sequence of inverse permutations , also easily derived given . It is a symmetric key that both the source and destination must share.
As a function of the values selected for the security parameters, , , , , and , there is a risk of collision, i.e., a repeated message value is signed and encrypted the same way.
(Collision). A collision arises when a reoccurring message consisting of quantum blocks, each of them representing a -qubit state, is re-numbered with the same sequence of integers , modulo , re-resigned with the same sequence of Clifford operators , chosen in the group , and re-encrypted with the same sequence of permutations , chosen in the symmetric group . The same numbering, Clifford operators, and permutations are picked twice to sign and encrypt a repeating message content.
The smaller the collision probability, the better, because collisions leak information. They make it possible to identify traffic patterns, which can eventually lead to breaking encryption schemes. For the analysis, let us assume that a quantum block state is a single member of the orthonormal basis, i.e., no superposition. A message consists of column vectors in the basis . It is assumed that all members of the basis are equally probable. It is also assumed that, for a message, all block numbering sequences of integers module are equally probable. These assumptions are reasonable, particularly when diffusion before encryption and assembly after decryption are done.
There are unique combinations consisting of a message of blocks of qubits, a numbering sequence of -bit integers, a sequence of Clifford operators chosen among a set of available operators, and a sequence of permutations chosen among a set of available permutations. When over messages are authenticated and encrypted with the same session key, at least one collision has occurred. We calculate the collision probability when less than messages have been encrypted with the same session key. Note that collisions are unavoidable with finite-length fields, determined in this case by the security parameters.
Let be the number of messages consisting of quantum states in authenticated using Clifford operators, chosen in subset , included in , of Clifford operators, and encrypted with permutations, chosen in subset , included in , of permutations. is the number of signature qubits allocated for each block. Let be greater than zero and less than equal to . When messages have been encrypted, the probability that at least one collision has occurred, denoted as , is at least but not greater than .
Let us assume that all messages are equally probable, that the choice of Clifford operators and permutations is uniform, and that probabilities are independent across messages.
Lower bound. The absence of collision after encrypting messages is represented as the event . The event corresponds to a condition where messages have been authenticated and encrypted. When no collision has occurred after the authentication and encryption of messages, it means that among the available combinations of message value, numbering sequence, Clifford operator sequence, and permutation sequence, solely combinations have not been used. Therefore, the probability of no collision when the -th message is signed and encrypted is
It follows that the probability of the absence of collision after the completion of the signature and encryption of messages is
Leveraging the inequality , with , the fact , and the equality , the product of Equation (18) is less than equal to
Leveraging the inequality , Equation (20) is greater than
Upper bound. Let the event denote a collision resulting from the th block encryption. The probability of is
Due to the existence of of unique triples comprising a message, a Clifford operator, and a permutation, we obtain that
□
The collision probability approaches the value of one-half by growing the block size () and number of blocks in a message (). It is upper bounded by the value one-half because the weight of the subtrahend one is progressively diminishing, in the numerator , with reaching .
Figure 1 plots the collision probability (-axis) versus the number of transmitted messages (-axis), from one to . The message size () is one. There are curves for two-, three-, four-, and five-qubit QPP (). The corresponding numbers of gates are 56, 17, six, and three. As mentioned in Remark 1, in the analysis, the maximum collision probability is one-half (or on the logarithmic -axis) when the number of encrypted blocks is equal to . Of course, when is greater than equal to , the probability is one. From this perspective, i.e., from the block-key point of view, the collision probability is noticeably high for a low number of encrypted blocks.
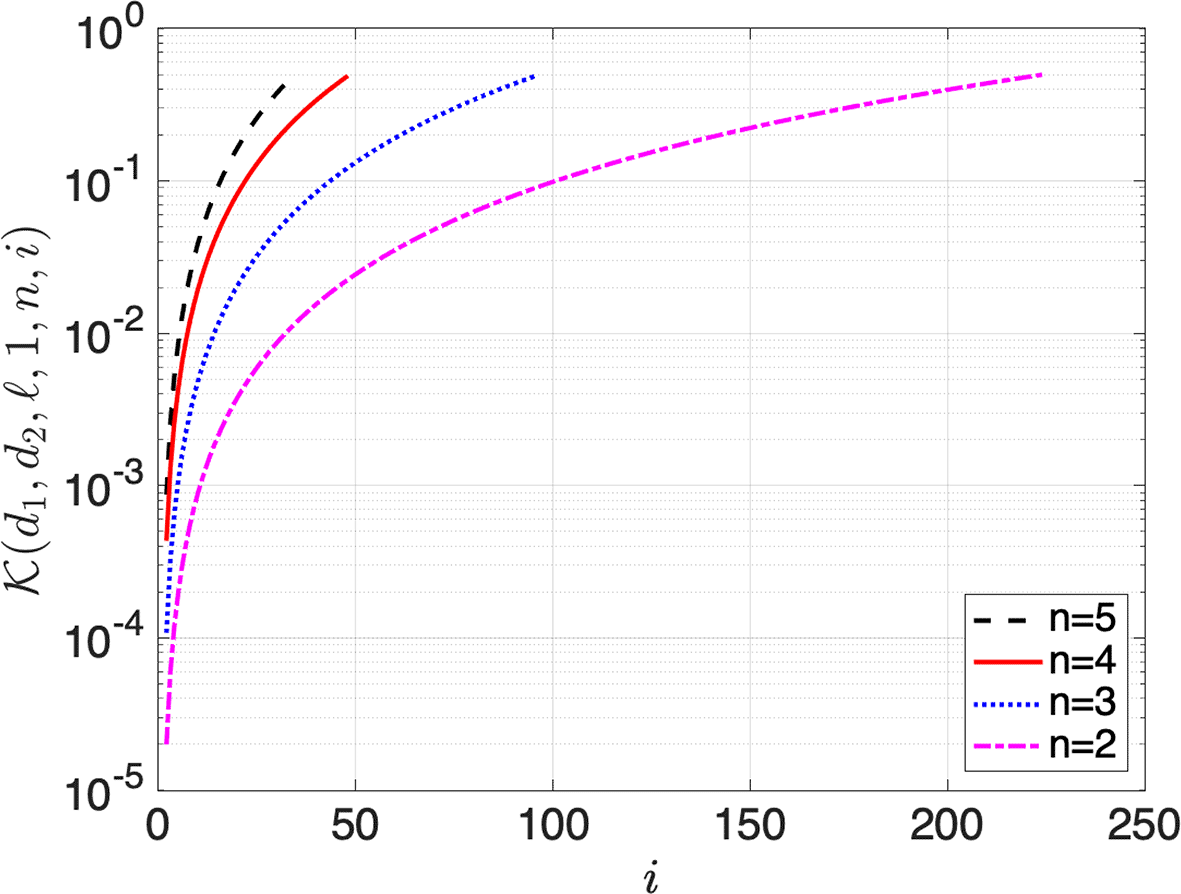
Figure 2 presents the message-key point of view. The -axis corresponds to the block size (), while the -axis represents the value of as a function of the number of blocks in a message () and the block size (). Again, as noted in Remark 1, in the analysis, the collision probability approaches value one-half as the number of blocks in a message () and the block size () grow and approaches . Figure 2 plots values for (Theorem 2) for block sizes two, three, four, and five and message sizes one, two, four, and eight. is a parameter to consider when conducting a risk assessment and determining the maximum number of messages that can be sent before renewing a session key.
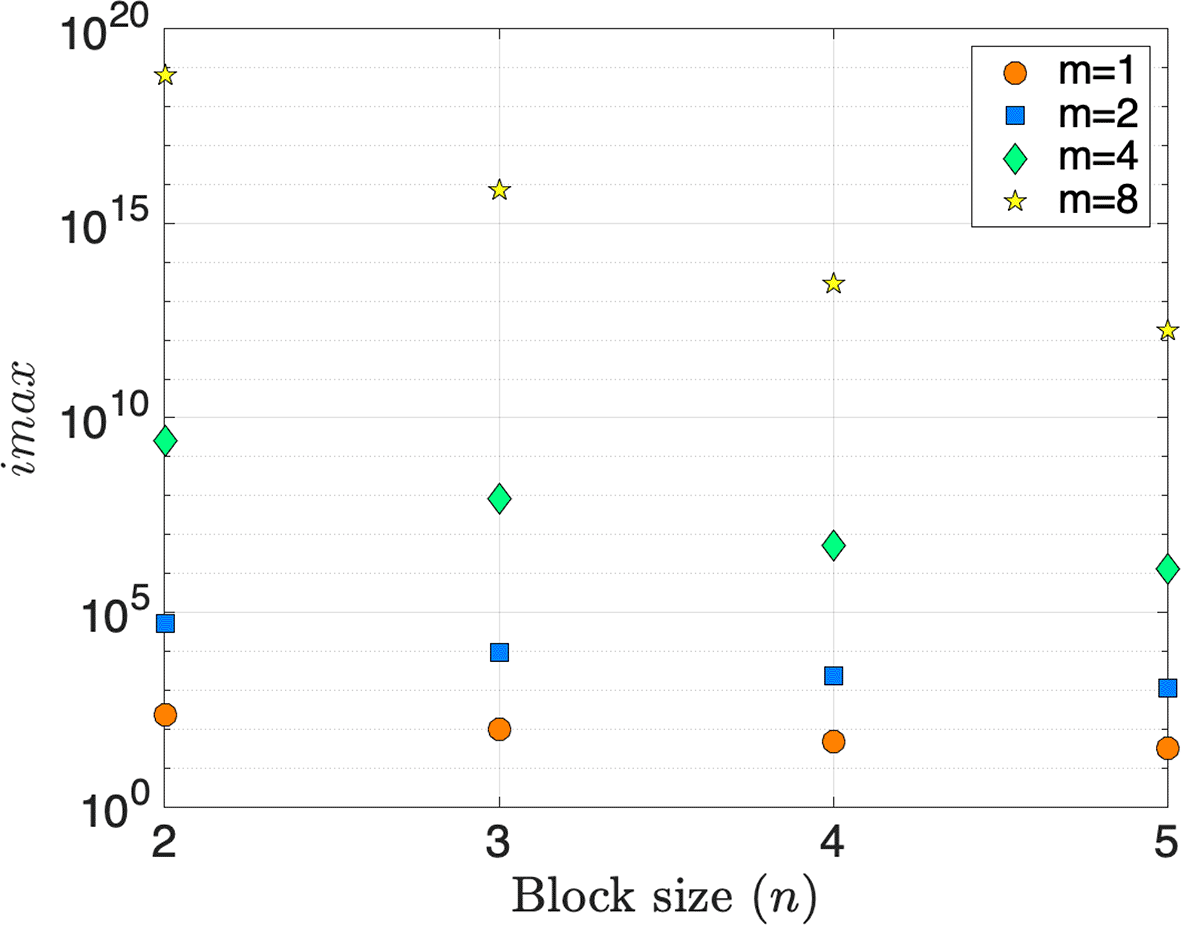
Security parameters and , selected according to the block size, are as suggested by Kuang and Perepechaenko.27 is equal to two.
An authentication and encryption scheme for quantum messages consisting of blocks of qubits has been presented. The scheme is simple and considers the scarcity of qubits for the upcoming first-generation quantum Internet. The authentication and verification key consists of a sequence of quantum Clifford operators. The encryption and decryption key is made of a sequence of quantum permutations. The scheme uses the block counter mode. Integrity and replay protection are also provided. For authentication, the source provides proof of ownership of the authentication key to the destination. Validation of integrity and replay protection rely on testing the consistency of the signature field of every block. The scheme is practical but does not achieve perfect indistinguishability because of the risk of message collision. This is normal and unavoidable when fixed-size fields are assumed to make a scheme practical. The message collision probability has been analytically determined. The model can be used to determine the values of the security parameters and the lifetime of session keys to mitigate the risk of information leakage according to the needs of the scheme’s users.
Zenodo. Quantum Data Communication Protection with the Quantum Permutation Pad Block Cipher in Counter Mode and Clifford Operators https://doi.org/10.5281/zenodo.8246914.
This project contains the following underlying data:
Data are available under the terms of the Creative Commons Attribution 4.0 International license (CC-BY 4.0).
| Views | Downloads | |
|---|---|---|
| F1000Research | - | - |
|
PubMed Central
Data from PMC are received and updated monthly.
|
- | - |
Is the work clearly and accurately presented and does it cite the current literature?
Yes
Is the study design appropriate and is the work technically sound?
Yes
Are sufficient details of methods and analysis provided to allow replication by others?
Yes
If applicable, is the statistical analysis and its interpretation appropriate?
I cannot comment. A qualified statistician is required.
Are all the source data underlying the results available to ensure full reproducibility?
Yes
Are the conclusions drawn adequately supported by the results?
Yes
Competing Interests: No competing interests were disclosed.
Reviewer Expertise: Quantum communication and cybersecuirty schemes
Alongside their report, reviewers assign a status to the article:
| Invited Reviewers | |
|---|---|
| 1 | |
|
Version 1 11 Sep 23 |
read |
Provide sufficient details of any financial or non-financial competing interests to enable users to assess whether your comments might lead a reasonable person to question your impartiality. Consider the following examples, but note that this is not an exhaustive list:
Sign up for content alerts and receive a weekly or monthly email with all newly published articles
Already registered? Sign in
The email address should be the one you originally registered with F1000.
You registered with F1000 via Google, so we cannot reset your password.
To sign in, please click here.
If you still need help with your Google account password, please click here.
You registered with F1000 via Facebook, so we cannot reset your password.
To sign in, please click here.
If you still need help with your Facebook account password, please click here.
If your email address is registered with us, we will email you instructions to reset your password.
If you think you should have received this email but it has not arrived, please check your spam filters and/or contact for further assistance.
Comments on this article Comments (0)